Ultimate Guide to Risk Assessments + Template
Take control of organizational risks by conducting a comprehensive business threat assessment. By understanding the likelihood and potential impact of critical events, you can proactively safeguard your operations.

“The best and most universal thing everybody can do is be informed,” says Sara Pratley, our Senior Vice President of Global Intelligence at AlertMedia. With threats escalating around the world, many of them impact businesses—if not directly, then indirectly. Can you name all the potential threats to your employees and operations?
Below, we’ll provide a framework for the risk assessment process and discuss how to use this analysis to protect your employees, facilities, and critical infrastructure. We’ll also explore tools—like a fill-in-the-blank risk assessment template—and strategies for more effectively monitoring, identifying, and communicating about threats that may impact your organization.
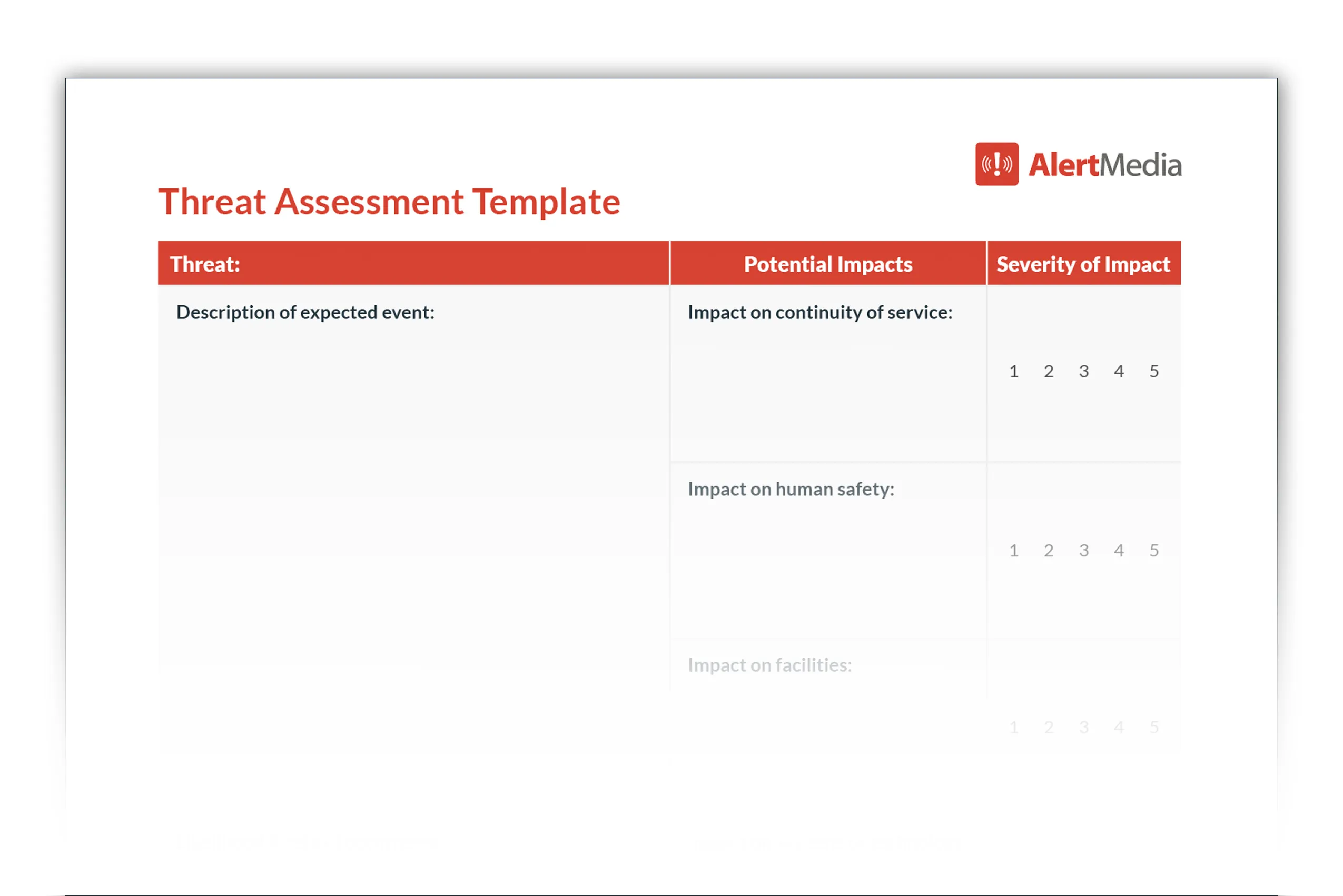
Download Our Threat Assessment Template
“It’s important to pay attention to what happened in the past, what’s been trending in recent years, and what’s happening currently to understand what’s likely to come in the future.”
—Sara Pratley, SVP of Global Intelligence at AlertMedia
How to Conduct a Risk Assessment
This video will help you facilitate an effective risk assessment at your organization.
What Is a Risk Assessment?
A risk assessment—sometimes called a threat assessment—evaluates the likelihood and impact of a risk or perceived threat. It is an integral part of a risk management plan. In practice, the term has multiple meanings. From corporate security to school safety, the phrase “risk assessment” can be used in different contexts:

- Cybersecurity risk assessment: IT and information security teams perform cybersecurity threat assessments to identify potential vulnerabilities and security gaps. The findings are used to develop strategies to protect against data breaches, targeted attacks, and other technology-related security risks.
- School/university risk assessment: According to the National Association of School Psychologists, “threat assessment involves determining whether a student poses a threat of violence.” School districts and educators use behavioral threat assessments as a critical part of school safety and violence prevention strategies. School staff, school administrators, law enforcement, and mental health professionals develop the risk assessment in collaboration. The purpose is to identify potential hazards of future acts of violence from students. School officials and the student’s parents can develop intervention plans, active shooter preparedness, and safe school strategies by analyzing key risk factors- such as a history of threatening behavior.
- Organizational risk assessment: A business threat assessment is typically performed by a cross-functional team composed of representatives from different parts of the business. The purpose is to identify and evaluate all events—from severe weather to supply chain disruptions to violent behavior—that can adversely affect personnel, operations, or critical assets.
This article focuses on organizational assessments of employee safety hazards and threats to business continuity. Still, organizations can use the risk assessment form and overall toolkit for any threat assessment program. With the information gained from a business risk assessment, your organization can develop risk mitigation strategies to protect employees, business operations, and facilities from potentially dangerous or disruptive events.
If you need more guidance on how to put this together, check out our comprehensive risk assessment template.
The Benefit of Regular Risk Assessments
Internal and external factors influence how you operate and plan for the future. And all types of risks are full of uncertainty. No technology can predict sudden storms, hurricanes, earthquakes, or tsunamis with absolute accuracy. Economic setbacks in one part of the world can create ripple effects across the globe. Meanwhile, as new technology and software emerge, bad actors continually find ways to exploit vulnerabilities. With the range of threats businesses face, a high level of unpredictability demands ongoing vigilance.
Regular risk assessments allow organizations to step back and reevaluate the threat landscape with a fresh perspective. For example, the supply chain risks your company faced from a labor strike in Europe may have subsided, but now you could be dealing with a new challenge in the form of stricter compliance requirements. Regular assessments help you adjust your risk profile, address emerging risks, and ensure your strategies remain relevant and practical.
For example, AlertMedia’s 2025 Threat Outlook Report analyzed key trends that shaped 2024 and will continue to impact industries in 2025, including:
| Environmental risks | Economic challenges | Cybersecurity threats | Geopolitical risks |
| Increasing extreme weather events like floods, storms, and hurricanes disrupt operations and threaten infrastructure. | Rising inflation, labor strikes, and supply chain disruptions create uncertainty for businesses. | Cyberattacks, data breaches, and ransomware incidents continue to grow in frequency and impact. | Political instability, conflicts, and public health concerns complicate travel planning and global operations. |
Understanding how your businesses may be impacted by these emerging risks or any of the others included in the 2025 Threat Outlook Report can help you better prepare and allot resources for any emergency that might occur. Promoting overall risk awareness is more than just a competitive advantage; staying operational in today’s complicated global risk landscape is crucial.
How to Determine Your Risk Profile
A risk profile can apply to an entire organization or break down into individual, product, asset, or project-management-based listings. These profiles encompass all the entity’s threats and provide a detailed analysis of their likelihood and potential impact. Specifically, it should cover:
- Type of risk: A detailed risk description of threats.
- Likelihood: An evaluation of how likely each risk is to occur—using data, trends, and expert analysis.
- Impact: A measure of the potential consequences for operations, finances, or employee safety.
- Mitigation plans: Detailed strategies to reduce or eliminate the identified risks.
- Monitoring approach: Systems and processes to track risks and adapt as circumstances change.
These items are typically assigned numerical values and charted to visualize their relationship to the organization’s priorities, risk thresholds, and available resources. This risk analysis helps prioritize which threats require immediate attention and informs strategic decision-making based on the organization’s risk appetite or risk tolerance.
Risk appetite vs. risk tolerance
All businesses require some level of risk to progress and grow. However, there is a fine line between taking strategic risks and acting recklessly. In addition, inaction poses a threat, as it can leave a business unable to keep up with competitors or adapt to changing market conditions.
For example, consider a logistics company so concerned about the threat of hurricanes that it chooses not to do business in Florida. While this decision helps the company avoid occasional power outages, storm damage, or stranded trucks, it comes at the cost of forfeiting millions of dollars in potential revenue from the third-most-populated state in the U.S. Meanwhile, competitors establish a strong foothold in the region, building brand recognition and customer loyalty. When the company decides to enter the market, it struggles to compete effectively. In this case, refusing to accept risk became a much greater liability.
A risk appetite defines and clarifies the level of risk a business is willing to accept in pursuit of its goals. A well-defined risk appetite helps organizations balance caution and opportunity, ensuring they take calculated risks that align with their strategic objectives.
Risk appetite is sometimes used interchangeably with risk tolerance, but these are two distinct concepts. Risk appetite refers to the overall level of risk an organization is willing to accept to achieve its strategic objectives, serving as a broad guideline. In contrast, risk tolerance defines the specific thresholds within that appetite, outlining how much variation from the acceptable level of risk is manageable in day-to-day operations.
Returning to the logistics company example—the company’s risk appetite allows it to operate in Florida. However, leaders set a risk tolerance that manages the exposure related to their threat, determining they can tolerate disruptions that affect up to 10% of the fleet during hurricane season but no more.
To stay within this tolerance, the company could take proactive steps such as pre-positioning inventory in nearby states, establishing alternative transportation routes, or halting operations in specific areas when a hurricane warning is issued. This balance ensures the company pursues high-revenue opportunities while keeping risks within acceptable limits.
Of course, this requires a deep understanding of your organization and its goals. That’s why it’s essential to bring together a multidisciplinary team to conduct risk assessments.
Building Your Threat Assessment Team
A risk assessment team should include stakeholders from departments across your organization who have a role in safety and security. At a minimum, it should consist of some executive, human resources, and facilities management team members.
The team members will convene to identify, evaluate, and develop prevention and mitigation strategies for various threats your business may face. It may also be necessary to include external stakeholders and partners who play a role in emergency response plans, such as local law enforcement officials and mental health professionals.
Internal and external roles to consider | |
Internal team members | External stakeholders |
|
|
How to Conduct a Risk Assessment
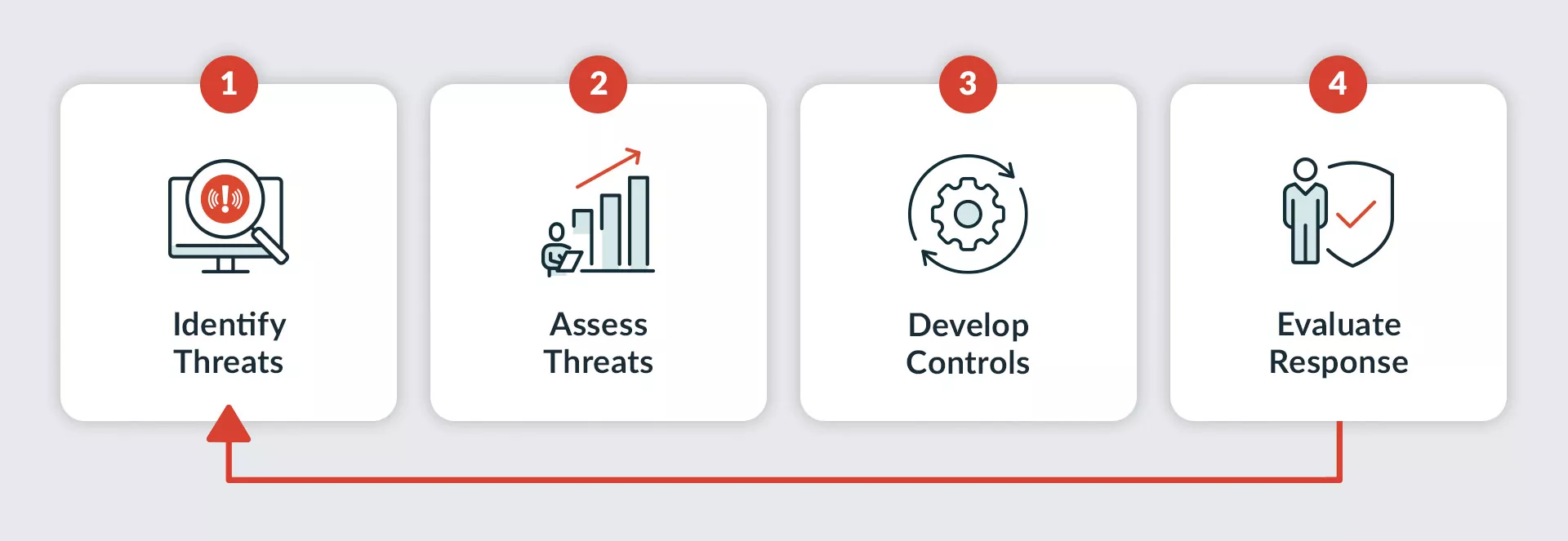
With your risk assessment team established, it’s time to get to work. Here are the four iterative steps to conducting a business threat assessment:
 Business Threat Assessment Cycle
Business Threat Assessment CycleStep 1: Identify hazards and threats
The first question you need to ask is: What are the threats? Ensure you are aware of the broad array of hazards and threats in business that could impact your people and assets. We have listed some risk assessment examples related to both external and internal risks.
External threat examples
- Meteorological: Hurricanes, severe thunderstorms, blizzards, tropical storms
- Geological: Earthquakes, wildfires, tsunamis, landslides, floods
- Biological: Disease outbreaks, pandemics, illnesses
- Transportation & supply: Significant road closures, widespread flight delays, supply chain disruptions
- Communications: Cell coverage outages, power outages
- Violent acts: Active shooters, civil disturbances, bomb threats
Go through the threats listed above and ask yourself: How would this impact my organization?
To answer this question, consider the nature of your business and work environments. If you are a software company with just one office located in Texas, for example, your risks will look substantially different than those of a large manufacturing company with offices scattered around the Northeast.
Also, consider remote workers and traveling employees. You have a duty of care to keep your employees safe, no matter where or how they work. Using a threat intelligence solution can help you proactively monitor and communicate about all external threats, including those that impact your remote and mobile employees.
Internal threat examples
- Information technology: Internet outages, systems downtime, corrupted data
- Utility outage: Electrical power, water, sewage, air conditioning/heating
- Accidents: Workplace accidents, structural collapse, mechanical breakdown
- Hazardous materials: Chemical spill, gas leak, radiological accident
External threats require monitoring broader variables, but internal threats are often more readily apparent. Some internal threats are universal (e.g., Wi-Fi outages), but most are company-specific. For example, you might look at your internal supply chain and ask yourself: Where could things go wrong? How could we build supply chain resilience? If your operations involve hazardous materials, you must have a hazmat safety plan. If your office building has a set of stairs prone to accidents, put up a sign warning people to “watch your step.”
Assessing internal threats requires a comprehensive risk analysis of your business, from stakeholders in facilities to IT to personnel. Using the bulleted list above as a starting point, consider which threats impact your operations—and how. Consider conducting an insider threat assessment to identify any risks to your organization that arise from an internal party’s access to your systems, assets, or data.
Tips for school threat assessments
Using a risk assessment tool for K–12 schools or universities is similar to business threat assessment models. However, you assess threats within the student population instead of looking for environmental threats. Threats such as untreated mental illness, targeted violence, bullying, and even more serious school shootings or public safety threats present in slightly different ways than business threats. Identifying these threats typically involves student interviews, peer group monitoring, warning signs of potential risks, conversations with staff members, and possibly witness interviews to gather information about past incidents. Once you’ve identified the threats, you can assess your level of concern and create a management plan, just like you would for a business threat assessment.
Step 2: Assess threats
Once you have identified the threats to your business, you need a way to evaluate the impact and risk likelihood.
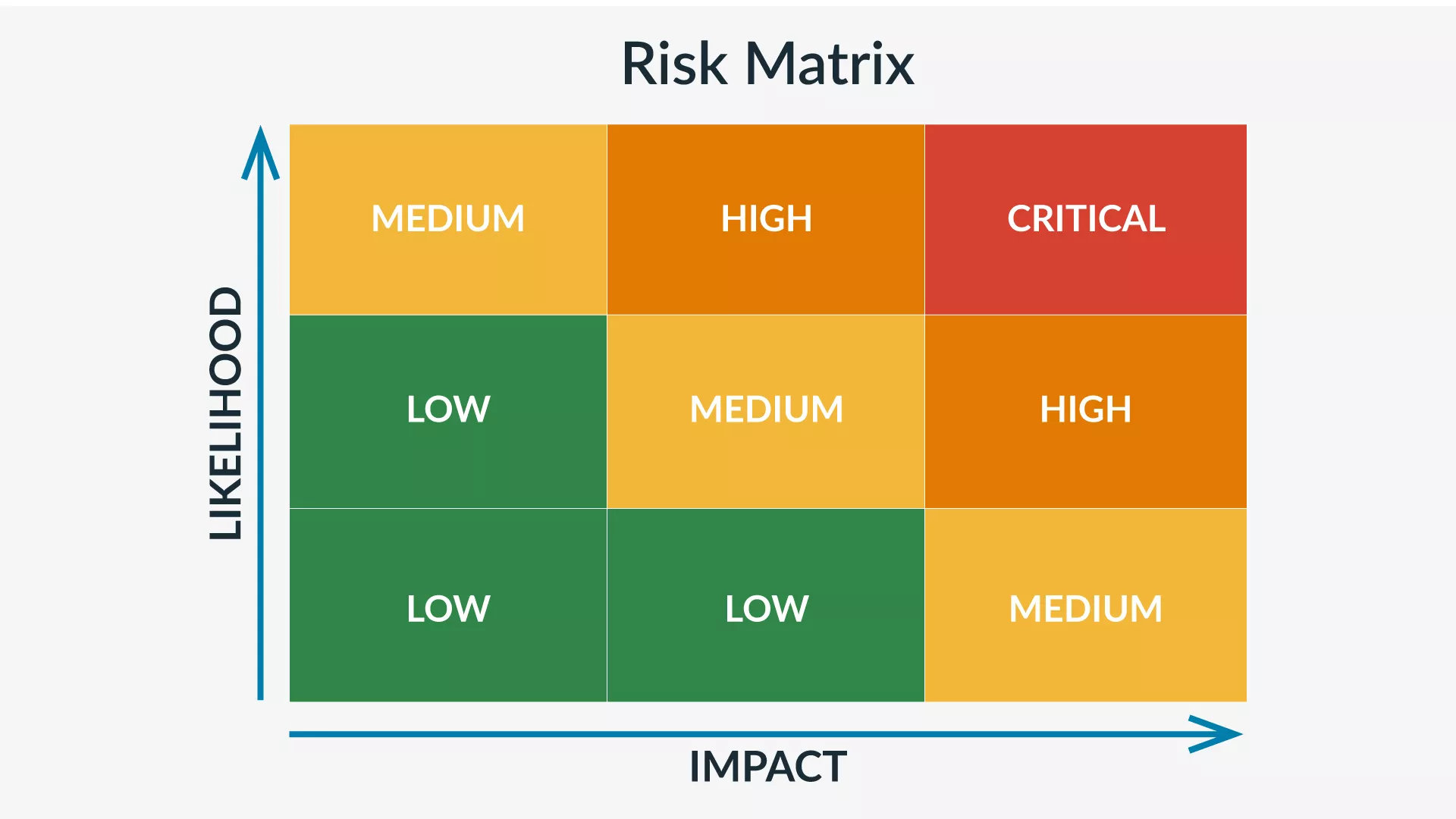
A risk matrix—also called a probability matrix or impact matrix—supports the threat assessment. The matrix helps assess each threat based on 1) the likelihood that the threat will occur and 2) the potential impact the threat will have on your business.
 Risk Assessment Matrix
Risk Assessment MatrixLikelihood
Certain factors increase the likelihood of a threat occurring. Location and history are both important risk factors to consider when evaluating the probability of a threat. When completing a risk assessment matrix, you rank the likelihood of the threat occurring on a five-point scale from improbable to frequent.
A company in California, for example, has a high chance of being impacted by an earthquake or wildfire, while a New England company has a low one. Similarly, a company in a major metropolitan city is more likely to be affected by civil disturbances than one in a sleepy suburban town, and it may invest in a more thorough physical security assessment to determine its specific risk rating.
It’s common for large companies to have many office locations across the country, even across the world. Each of these locations has its own set of potential hazards. With many employees working remotely or traveling on a work trip, employers must consider all locations employees work from—not just where the company’s facilities are located. Travel risk assessments can help you determine risks away from the office.
Impact
The impact of a potential risk is the amount of damage or harm the threat could create. On a risk assessment matrix, the severity of a threat ranks on a four-point scale from negligible to catastrophic.
When assessing threats, consider all the different types of impact. Impact can be divided into three broad categories: people, locations, and assets. From employee safety to financial loss and reputation harm, a threat can negatively affect your business in various ways.
Consider these two different threats as examples for assessment: 1) the threat of a winter storm and 2) the threat of your CEO dying. The first threat has a medium impact but a high likelihood. Winter storms are guaranteed if you’re located in the Northeast—but they shouldn’t derail your business. The second threat, on the other hand, has a high impact but a low likelihood. It is unlikely that your CEO will die suddenly—but it would have a huge impact. During this analysis, you might conclude that a winter storm is high risk, whereas the CEO dying is medium risk.
These scenarios are given a numerical risk rating that can be tracked and managed over time as risks change. This system allows you to prioritize your responses and adjust them as new information becomes available or circumstances evolve.
For example, if you rate a supplier’s delivery delays as high-risk during a global shortage, you’ll want to prioritize mitigation efforts like securing alternative suppliers or increasing inventory stock. Once the shortage is resolved and the supplier’s reliability improves, you can lower the risk rating and shift focus to other pressing needs.
Document your methodical analysis of each threat’s likelihood and impact. Our threat assessment template is a great place to start.
Step 3: Develop control measures
Once you have identified the potential threats and you have a way to quantify the impact, you need to plan your response. This means implementing controls that mitigate the threats you’ve identified.
You will want to look at your overall risks and decide which actions your business can take to reduce each risk. For most risks, this means both:
- How do we decrease the likelihood that this will happen?
- How do we decrease the impact if this does happen?
For example, if you’re a business in Chicago, you are guaranteed to face a winter storm. While there is not much you can do to prevent a storm from happening, you can minimize the disruption that a winter storm will have on business operations—the impact. On the other hand, if employees must work or travel in a region with high crime rates, you may want to focus on reducing the likelihood and impact of safety threats on your people.
Regardless of the risk, here are a few specific controls you can implement:
Train employees
Employee threat assessment training is the first and most basic control in business risk management. Risk mitigation can’t just exist in one department or one person. Although it may start in your business continuity and disaster recovery (BC/DR) division, it can’t end there.
Ensure your entire organization knows and understands what threats may occur. Train individual on how these threats may impact their role and the business as a whole. This training will help them better understand the response plan and how they should act during an emergency—especially for high-likelihood threats. Often, the most effective employee training involves active participation. Most companies conduct fire drills—but don’t stop there. Also, consider the wide range of tabletop exercises your company can implement to offer practice for various threats.
Create policies
In addition to training employees, create threat assessment procedures and guidelines to mitigate the identified threats. For example, in the event of a severe winter storm, you need a policy for how you will notify employees of delays or closures. Develop a comprehensive corporate travel policy to keep traveling employees safe from the variety of threats they may encounter.
Your threat assessment procedures should indicate when third parties—such as law enforcement or mental health services—need to be involved. For example, when threats of violence arise, it is necessary to report them to and involve local law enforcement officials.
Document emergency response plans
Every emergency management professional will tell you that the best time to prepare for an emergency is well before it occurs. Creating an emergency response plan—a documented series of steps your organization will take during an emergency—can help ensure employee safety and minimize the impact on critical operations.
Emergency response plans help organizations address various threats, such as hurricanes, wildfires, winter weather, chemical spills, disease outbreaks, and other hazards. The goal is to reduce or prevent human injury and property damage during threatening situations by documenting the steps for a timely response tailored to each scenario.
Step 4: Evaluate your response
The final step in a business threat assessment is what makes the risk assessment process iterative. Once you have identified a threat, assessed its impact, and responded, you must assess your response.
Here are the questions you need to ask:
- Was this a threat our organization had identified?
- Did we properly assess the likelihood of this threat?
- Did we properly evaluate the impact of this threat?
- Was this threat avoidable?
- What controls did we have in place for this threat?
- How effective were our controls?
- How quickly were we able to respond?
- Was our communication effective?
- Did we have the proper resources to address the threat?
Once you have answered these questions, it’s time to turn to the big question: What can we do better? You will never have the perfect response to a given threat. Even when you execute your plan down to the letter, look for ways to improve it based on how it worked. Don’t let good be the enemy of great.
Talk to employees—especially those directly impacted by the threat. By soliciting employee feedback, you can uncover weaknesses in your plan that you may not have recognized otherwise. One effective way to conduct this follow-up is to send out an employee survey. Your employees will likely have ideas for ways you can prepare them to respond more effectively to the threat.
Once you have evaluated your response and identified areas for improvement, go back to Step 1. Repeat the process, integrating the new relevant information and feedback you have received.
—Sara Pratley, VP of Global Intelligence, AlertMedia
Specialized Risk Assessment Examples
The above sections suit a general risk assessment you can adapt to your organization’s unique threats. However, specific risks will require adjustments to the Identify, Assess, Develop, and Evaluate cycle. Below is a list of common risk types and considerations specific to their assessments:
| Civil unrest | Environmental risks | Operational risk | Supply chain risks |
Civil unrest
Civil unrest might seem like a far-off concept, but protests, riots, or political instability can disrupt operations anywhere with little notice. When the worst happens, it will be chaotic, and your team may not have access to local resources or support. Below are some specific considerations for dealing with this threat.
- Implement tools and partnerships (e.g., security firms or government alerts) to receive live updates on protests, riots, or unrest near your facilities.
- Build relationships with local leaders or community organizations to understand regional tensions better and receive early warnings of potential unrest.
- Reinforce physical security measures, such as perimeter fencing, shatterproof windows, and controlled access points.
Compliance risks
Compliance is an ever-growing challenge, especially for global organizations, as they must navigate a complex web of regulations such as OSHA, GDPR, and CCPA. Failure to comply with standards can expose businesses to various risks, including financial penalties, legal challenges, and reputational harm. In some cases, non-compliance may even result in restrictions on operating in key markets. Organizations should adopt targeted strategies and proactive measures to address these risks effectively.
- Establish a dedicated compliance team or use specialized tools to monitor upcoming regulatory changes globally, including industry-specific requirements like OSHA for workplace safety or GDPR for data protection.
- Designate in-country compliance representatives who can provide localized insights into evolving regulations and identify specific types of risk relevant to their region.
- Use technology to automate processes such as reporting, documentation, and alerts for regulatory deadlines.
Cybersecurity risks
All the same threats of phishing, ransomware, and data breaches remain, but we’ve seen a new threat emerge to businesses worldwide with the widespread adoption of AI. Use these tools to craft more sophisticated phishing attacks, automate vulnerability scanning, and even mimic human behavior to bypass traditional security measures. Here are suggestions for how to adapt:
- Invest in cybersecurity solutions that use AI and machine learning to identify patterns of malicious activity, such as advanced phishing attempts or unusual network behavior.
- Implement multi-factor authentication (MFA) combined with biometric or behavioral verification to defend against AI-driven credential attacks or identity spoofing.
- Develop guidelines for employee use of AI tools, monitor AI-generated content for security vulnerabilities, and ensure compliance with data protection laws when using AI platforms.
Environmental risks
Climate change continues to lead to unprecedented natural disasters like hurricanes, earthquakes, and wildfires. These events are growing in severity and can cause physical damage to facilities and longer-term disruptions to operations. To stay prepared:
- Conduct detailed assessments of your facilities to identify their vulnerability to natural disasters and prioritize risk mitigation efforts for high-risk locations.
- Invest in resilient building materials, flood barriers, and fire-resistant designs to minimize damage during severe weather events.
- Establish relationships with alternative suppliers, logistics providers, and backup facilities to resume operations quickly during prolonged disruptions.
Financial risks
Financial risks often come hand in hand with other threats to your operations. For example, the conflicts in Ukraine and Israel have led to rising energy costs, supply chain disruptions, and market volatility that impact businesses globally. Just about every risk on this list will have an accompanying financial impact. To mitigate these threats:
- Develop financial models to predict potential geopolitical or market disruptions impacts, including increased costs, currency fluctuations, or credit availability issues.
- Negotiate multi-region supplier agreements to reduce dependence on a single source or market and protect against price spikes or shortages.
- Implement flexible pricing models to account for fluctuating costs while maintaining profitability and customer trust.
Health and safety
COVID-19 ushered in new health and safety threats for customers and employees. The pandemic highlighted the need for robust protocols to manage infectious diseases, but health and safety risks extend far beyond pandemics. From ergonomic issues in remote work setups to exposure to hazardous materials in industrial settings, organizations must proactively safeguard their people and operations.
- Regularly update workplace risk policies to address emerging health threats, including seasonal illnesses and airborne contaminants, with clear communication and training.
- Evaluate in-office and remote work environments for potential strain or injury risks, providing employees with appropriate tools or adjustments.
- Establish systems for rapid response to health crises, including access to medical resources, quarantine spaces, and mental health support.
Insider threats
In 2024, 83% of business leaders surveyed reported being victims of at least one insider attack, while almost half reported an increase in these incidents. While you can’t eliminate insider threats, proactive measures can significantly reduce the risk and impact. Here are some tips:
- Deploy monitoring solutions to detect unusual employee behavior, such as unauthorized access to sensitive data or downloads outside regular working hours.
- Implement access controls that require continuous verification, granting employees access only to the data and systems necessary for their roles.
- Ensure all access credentials are revoked immediately upon employee departure and conduct audits to verify compliance with data-handling policies.
Operational risk
An operational risk assessment focuses specifically on how processes, systems, and personnel contribute to potential disruptions in daily business activities. These risks can arise from human error, equipment failure, or external factors like supply chain issues. Addressing operational risks requires identifying vulnerabilities and implementing measures to ensure continuity and efficiency.
- Identify critical points in workflows where inefficiencies or failures could cause significant delays or disruptions and prioritize mitigation strategies.
- Implement backup systems and cross-train personnel to ensure seamless operation in case of equipment failure or staff unavailability.
- Regularly assess third-party providers’ reliability and contingency plans to minimize dependency on any single supplier or partner.
Physical security risks
Physical security risks are evolving as organizations move toward more dispersed workforces. While remote work might appear to simplify securing physical locations, it introduces new challenges. Now, organizations must monitor not just one location but multiple satellite offices and data centers. To manage these changing threats:
- Deploy centralized systems to monitor and control physical access to all facilities, including remote offices and data centers, with real-time alerts for unauthorized entry.
- Conduct periodic evaluations of all locations to identify vulnerabilities unique to each site, such as local crime rates or natural disaster risks.
- Use IoT-enabled devices and inventory systems to monitor the physical movement of valuable equipment, especially as employees work across multiple locations.
Reputation risks
In the modern information age, word spreads fast, as does negative public perception, scandals, or customer dissatisfaction. These events can damage your brand’s trust and credibility. Assessing reputation risks involves monitoring public sentiment and preparing response strategies.
- Use tools to track public sentiment in real time, identifying emerging issues before they escalate into full-blown crises.
- Regularly practice scenario-based crisis responses with your leadership and communications teams to ensure swift and effective action during actual events.
- Build trust by openly sharing updates on key company activities, such as sustainability efforts or community involvement, to mitigate the impact of adverse events.
Supply chain risks
Delays, shortages, or disruptions in the supply chain can have a domino effect on business operations. Assessments focus on identifying critical suppliers, potential disruptions, and developing alternative sourcing strategies.
- Evaluate supplier reliability through on-site visits or third-party audits.
- Create inventory buffers for high-demand products in case of disruptions.
- Use predictive analytics to forecast potential delays based on historical trends.
Workplace hazards
Workplace hazards remain a persistent challenge for organizations. They encompass various types of risk, including physical injuries, mental health challenges, and unsafe work practices. These risks can lead to lost productivity, legal liabilities, and damage to employee morale. Proactively identifying and addressing workplace hazards is essential to maintaining a safe and efficient environment.
- Conduct tailored risk evaluations for each job role and environment, addressing physical risks, ergonomic issues, and unsafe work practices to mitigate potential hazards effectively.
- Implement digital tools that enable employees to quickly report hazards or near misses. This will ensure prompt corrective actions and foster continuous safety improvement.
- Develop programs to address workplace stressors, combining resources such as counseling, flexible work arrangements, stress management training, and appropriate personal protective equipment for high-risk roles.
Workplace violence
Workplace violence is a growing threat, especially in healthcare environments where workers face attacks at triple the rate of those in other industries. The costs of these incidents go beyond physical and financial, taking an emotional toll on your workforce. To prepare:
- Provide employees, especially those in high-risk industries, with training on identifying warning signs and effectively diffusing potentially violent situations.
- Install panic buttons, surveillance cameras, and control measures in vulnerable areas to protect employees and deter incidents.
- Develop clear, step-by-step procedures for employees to follow during and after violent incidents, including immediate support and follow-up counseling services.
Taking Advantage of Threat Intelligence Technology
A proper business threat assessment requires modern technology to support it. You can’t expect to manually monitor the expanse of potential threats—especially when you have remote workers, multiple office locations, and traveling employees. Today’s landscape requires the newest technology for threat monitoring and emergency communication.
Using a modern emergency communication solution with integrated threat intelligence will enhance organizational resilience. Your business threat assessment is incomplete without it.
With AlertMedia’s unified threat intelligence and emergency communication software, you can easily monitor and notify employees about emerging threats that may impact them. Using comprehensive threat data from analysts, social media, and news outlets worldwide, AlertMedia performs over 100 million calculations daily to cross-reference the location of each global threat against employee and asset locations. This analysis allows companies to see the threats that impact their business easily.
For a risk assessment example, let’s say a hurricane is in the forecast for the Gulf Coast. Quality threat assessment engines quantify the impact of the threat (identifying which employees and offices are in the path of the storm)—and automatically update this impact assessment as the storm changes. Perhaps you have offices and remote employees in multiple locations near the Gulf Coast. As the path of the hurricane changes, real-time threat intelligence and impact assessments help you rapidly identify those in harm’s way to ensure they are informed and prepared.
If a situation requires personalized attention from experts, solutions that allow you to communicate directly with intelligence analysts can give you and your team a responsive, real-time resource when things get hectic. They can answer your specific questions and proactively keep an eye out for additional information, ensuring you can act on accurate, up-to-date, and relevant details.
Combined with powerful emergency communication capabilities—such as survey notifications, event pages, and multichannel messaging—systems such as AlertMedia enable organizations to proactively identify, mitigate, and respond to any threatening situations that may arise.
Why Resilience Hinges on Risk Awareness
While nobody likes to think about facing a threat that could jeopardize their people and business, risk assessments play a vital role in protecting your employees and operations. Conducting a business risk assessment will put your organization in the best position to respond to whatever threats come your way.
In a word, your company will be resilient. You will have an answer to even the most uncertain scenarios because you will have a plan ahead of time. With a comprehensive organizational risk assessment—backed by modern emergency communication and threat intelligence technology—you can strengthen your risk management and emergency preparedness capabilities to be ready for any emergency that may arise.