How to Master the Operational Risk Assessment and Keep Your Business Running Smoothly
Your business faces operational risk every day. With the right intel, communication, and internal processes, you can get ahead of risk before it threatens business continuity.

Are you worried about a supply chain issue crippling your company’s production? How about hackers using stolen credit card information for a wave of fake purchases? Situations like these could overwhelm your inventory, divert customer service and IT efforts, and frustrate customers and employees.
Operational risks, those snags in daily business processes, can trigger a domino effect across internal systems. The good news is, you don’t have to sit idly and wait. Operational risk management (ORM)—with the operational risk assessment as its cornerstone—allows you to identify and address potential threats before they snowball into major disruptions.
Read on to discover how to use operational risk assessments and proven strategies to manage operational risk events so you can keep critical workflows humming along.
Operational Risk Assessment Template
What Is Operational Risk Management?
Operational risk is the chance of loss or disturbance due to mistakes or breakdowns in a business’s operations. The risk could be a system failure, an employee mistake, a power outage, a lack of internal controls, a procedure that doesn’t go as planned, or anything in between. Basically, anything that costs you money or disrupts your normal operations is operational risk.
The Basel Committee on Banking Supervision (BCBS) originally developed the working definition of operational risk for the financial services industry. But it applies in a general sense to any type of business.
Common examples of operational risk include:
- Human error by employees, partners, or vendors
- Data breaches and other cybersecurity issues
- Technology risks tied to automation, artificial intelligence, and robotics
- Poor business processes and controls
- Product development and launch
- Natural disasters or other external events
- Internal and external fraud
- Workplace safety issues
Operational risk management is all about protecting your business from the everyday bumps and bruises that can turn into big problems. It’s a systematic method for identifying, assessing, and controlling risks that stem from your internal processes, people, and systems. ORM is similar to enterprise risk management (ERM) or corporate risk management (CRM), however, the scope is narrowed to focus solely on threats that could slow, halt, or add cost to day-to-day business operations.
Imagine it like this: Ideally, your business runs like a well-oiled machine. The ORM process helps you spot any loose cogs or glitches (like a missed safety check or faulty alarm system) in that machine before they cause a major interruption.
The main benefits of proactively managing operational risks should be fairly obvious: Your business avoids costly disruptions and financial losses, keeping the business profitable and running smoothly. Beyond that, though, ongoing risk mitigation supports better decision-making, improves overall operational resilience, and ensures your business can weather any storm. Operational risk assessments are a key piece of that.
How to Perform an Operational Risk Assessment
An operational risk assessment is a forward-thinking review of your everyday business activities to identify risks and their potential impacts. It helps you spot potential problems before they cause financial trouble, slowdowns, or other headaches. Essentially, it’s a process of documenting and assessing risks that could disrupt your operations so your company can address those risks and maintain business continuity.
1. Identify risks
The first step to operational risk management is knowing what you’re up against. Risk identification involves a thorough internal audit of people, processes, and systems. Review things like risk and incident history, supply chain and suppliers, existing safety protocols, and audit reports to find patterns or possible trends in past events. You should also collect employees’ input through interviews or surveys to understand the risks they encounter in their workspaces.
Remember, you’re looking for all types of risks, including everything from storms and technology threats to problematic employee practices and structural vulnerabilities.
2. Analyze impacts
After identifying potential hazards, the next step of the operational risk assessment process is to analyze the likelihood and possible impacts of these threats. How likely are the threats to occur? And how severe would the potential impacts be? Quantify the probability and impact of threats using a risk matrix (covered in more detail below).
With the help of an operational risk assessment matrix, you’ll build a prioritized list, making it clear where to begin focusing efforts. This guarantees that you’re tackling the most significant threats to your business first and puts your organization in the best position to protect your people, assets, and operations.
3. Determine management tactic
Green light or red flag? A critical element of the operational risk assessment is choosing the appropriate management tactic. The four common risk response strategies are:
- Avoid
- Transfer
- Mitigate
- Accept
If a risk is deemed “acceptable” (for example, granting slightly extended credit terms to a long-time customer) you may choose to proceed. However, if it’s too high (such as a restaurant ignoring repeated health code violations) you’ll need to brainstorm solutions to transfer, avoid, or mitigate the risk. This might involve adding safeguards, modifying the plan, or even changing course entirely.
With risk management, it’s crucial to assign decision-makers who understand the operational impacts and the pros and cons of each decision. The right call may not be obvious at the surface, so you need people at the wheel who are in tune with what’s at stake and how to make quick decisions.
4. Implement controls
With a clear picture of the risk landscape and its potential for impact, as well as a general approach to managing risk, it’s time for action. Risk mitigation controls act as guardrails, allowing your organization to limit risks or make them more manageable. Worried about theft? Security cameras and target hardening can deter it. Concerned about cyberattacks? Firewalls, spyware, and stronger access controls can be your shield.
Review existing controls (like safety procedures, prevention measures, and employee activities) to see what might be missing, and use that intel to build a plan. Strengthen existing controls or add new ones as needed to minimize the impact of each threat.
5. Monitor and reassess
Whatever you do, don’t set it and forget it. Your operational risk management program is ongoing, and you should continue monitoring, assessing, and iterating for the long term.
Set metrics for success, and regularly check that your controls are still working against evolving threats. If they’re not, you may need to adjust internal processes or implement new controls. This consistent monitoring keeps your organization adaptable and protects your operations from the risk of loss or shutdown.
4 Principles of Operational Risk Management
The U.S. Navy uses four core principles to guide its operational risk management approach. These principles can be particularly helpful in the risk decision process (step 3 above).
Accept risks when the benefits outweigh the cost
You’ve heard the saying “No risk, no reward.” Well, that’s the idea behind the first principle of operational risk management.
Sometimes, achieving your goals requires taking strategic risks—specifically, when the potential benefits of a risk outweigh the potential downsides. Or, it might be that there’s no alternative path to success. For example, if you’re in growth mode, you might be willing to accept more risk in exchange for opportunities to keep growing quickly.
Of course, you’ll want to carefully weigh the potential payoff against the threat of damage, and gain leadership buy-in before taking any risk.
Accept no unnecessary risks
Not all risks are worth taking. While some risks offer significant benefits, others provide little to no advantage, and could even cause serious problems.
For example, imagine rushing a new product to market without proper quality control. This might be seen as an “acceptable risk” when you consider what the product would add to the bottom line. However, if the potential for defects and customer dissatisfaction is high, the risk likely outweighs any potential reward.
The key to this principle is to avoid taking unnecessary risks, especially those with minimal benefits or weak mitigation plans.
Anticipate and manage risk by planning
The worst way to handle risk is to be caught off guard. That’s why operational risk management involves developing business continuity plans that outline how the company will respond to disruptions.
Think of it as having a backup plan for every aspect of your business. By anticipating potential issues and implementing controls (like data backups or alternative suppliers), you can minimize damage and keep operations running smoothly, even when the unexpected happens.
Let’s say, for example, your restaurant chain relies heavily on a single vendor for eggs, which are a main ingredient in multiple menu items. This creates a high operational risk, as any disruption at the supplier level could halt production. To defend against this risk, the company could identify potential backup suppliers and proactively build relationships with them. This “plan B” gives you options if your primary supplier encounters problems.
Make risk decisions at the appropriate level
Effective operational risk management means involving the right people at the right level. Empowering employees to identify and address potential issues within their area of expertise allows for quicker detection and risk control.
However, you need guardrails. The organization needs to establish a clear “risk appetite” based on what level of risk is acceptable and what isn’t. This empowers employees to make informed decisions while ensureing everyone is on the same page about what types of risk warrant escalation to higher management.
Imagine a salesperson hears of a potential regulatory change that could impact their product line. Empowered by the company’s risk management framework, they can flag this concern with their manager. Senior management, understanding the risk appetite for regulatory issues, can then decide whether it needs to be escalated to the legal team for further analysis.
Operational Risk Assessment Tools and Techniques
As with any type of threat assessment, the right approach depends on factors like your business’ industry, size, geographic location(s), and revenue model. That being said, there are a few operational risk assessment tools and techniques that tend to reappear time and again.
Risk matrices
A risk matrix offers a clear visual of your organization’s risks, highlighting both their likelihood and severity. Most risk matrices share a simple grid format. The Y-axis depicts the likelihood of a risk, and the X-axis shows the severity of its consequences (both ranging from very low to very high). Using this model, you can quantify and prioritize potential risks with a simple formula:
Likelihood x Consequence = Level of Risk
For example, a minor website outage during off-peak hours has a low likelihood of occurring because websites often have backups and redundancy built-in. The severity is also low because an outage outside of peak business hours would cause only minimal lost sales.
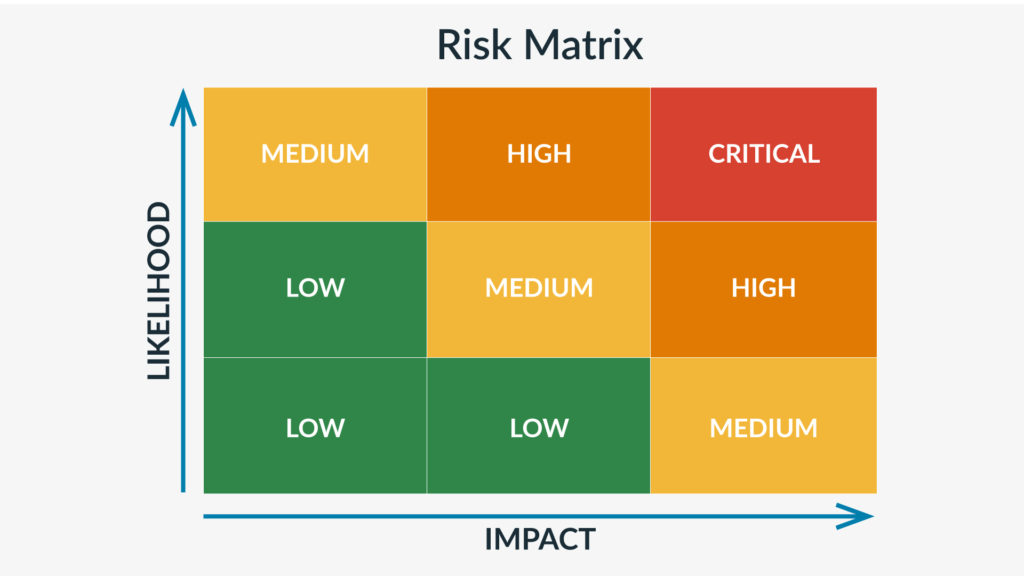
A cybersecurity attack with a successful data breach, on the other hand, might be a medium-high-likelihood, high-severity scenario. It’s medium-highly likely because cyberattacks are becoming increasingly common. And the severity is high because a data breach could expose sensitive information which could lead to lost customers. Plus, it would mean diverting employee time and labor to fixing the damage. This could cripple a business’s ability to operate and erode customer trust.
Using a risk matrix allows you to:
- Identify high-risk areas quickly
- Explain risks clearly to stakeholders
- Determine appropriate risk responses
- Prioritize risks and risk management activities
Threat intelligence solutions
Threat intelligence solutions act as an early warning system, which could give your business a vital head start in staying ahead of risks and safeguarding operations.
These solutions gather and analyze data from various sources, including weather warnings, industry trends, cybercrime reports, and dark web monitoring. Some solutions include human vetting by expert analysts to give you 24/7, real-time access to accurate information on emerging threats and ongoing attacks.
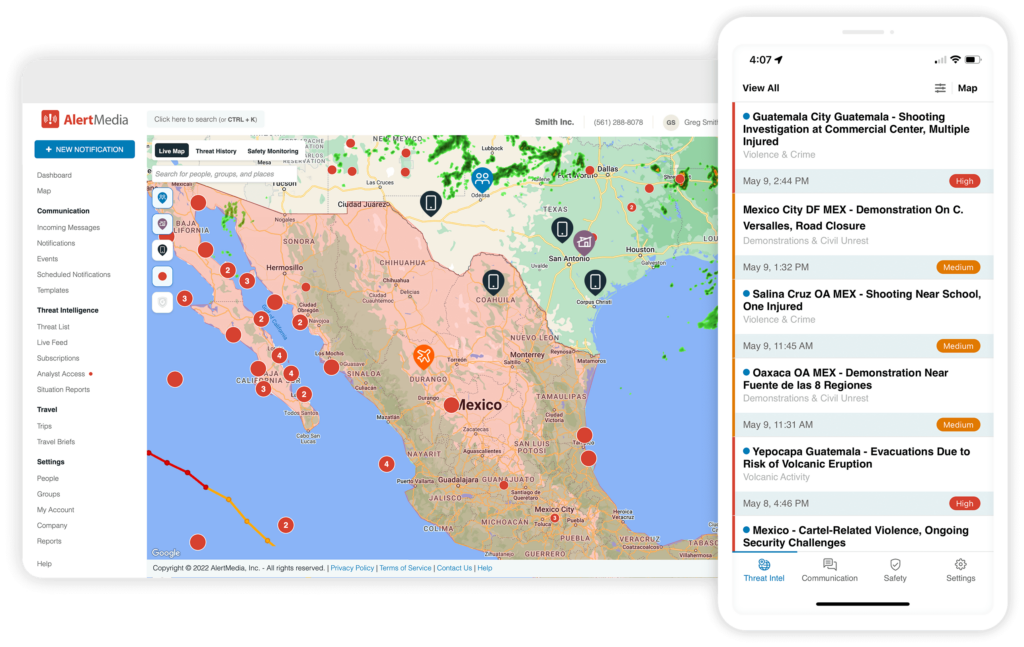
They also assist with risk prioritization and timing, letting you know the moment your people or assets are at risk. Automated alerts make it easy to inform every person who needs to know, via every channel necessary.
In-house or outsourced intelligence?
For safety leaders, it’s a big decision whether to keep threat intelligence in-house or outsource. Bart Brown, Vice President and Chief Security Officer at Frontier Communications, says threat intelligence is a great candidate for outsourcing. But the decision is multi-faceted. When considering outsourcing, Brown recommends:
- Verifying the capabilities and track record of potential vendors by reaching out to their current customers for benchmarking
- Treating outsourced teams as part of the organization
- Incorporating them into team meetings
- Providing them with the necessary training and understanding of the company’s mission
“I’m looking for a partner, not a vendor,” noted Brown on The Employee Safety Podcast. If a potential threat intelligence provider isn’t ready to evolve with your company and help you get better over time, it might not be the best fit.
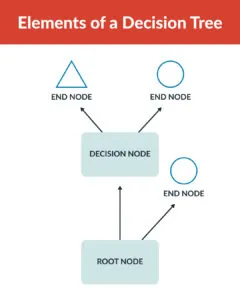
Decision trees
Decision trees give safety leaders a way to visualize and evaluate potential risks and their consequences systematically. This decision-making model is made up of nodes, branches, and end nodes:
- Nodes represent decision points or risk factors to be evaluated
- Branches represent the possible outcomes or risk scenarios
- End nodes show the final outcomes or risk levels—e.g. high, medium, low (also known as leaf nodes)
Decision trees provide a structured approach for organizations to dissect complex operational risks. By navigating the tree from the starting point, leaders can evaluate risk factors at each branch and reveal potential outcomes. Assigning probabilities and quantifying potential impacts along these branches allows for a comprehensive risk assessment.
Proactive Risk Planning Puts You Ahead of the Game
Your business faces operational risk every day—there’s no avoiding that. But a proactive approach helps you get in front of threats before they cause major damage. Ongoing planning and preparation have an aggregate effect on your ability to protect your people, processes, and assets from whatever comes your way.