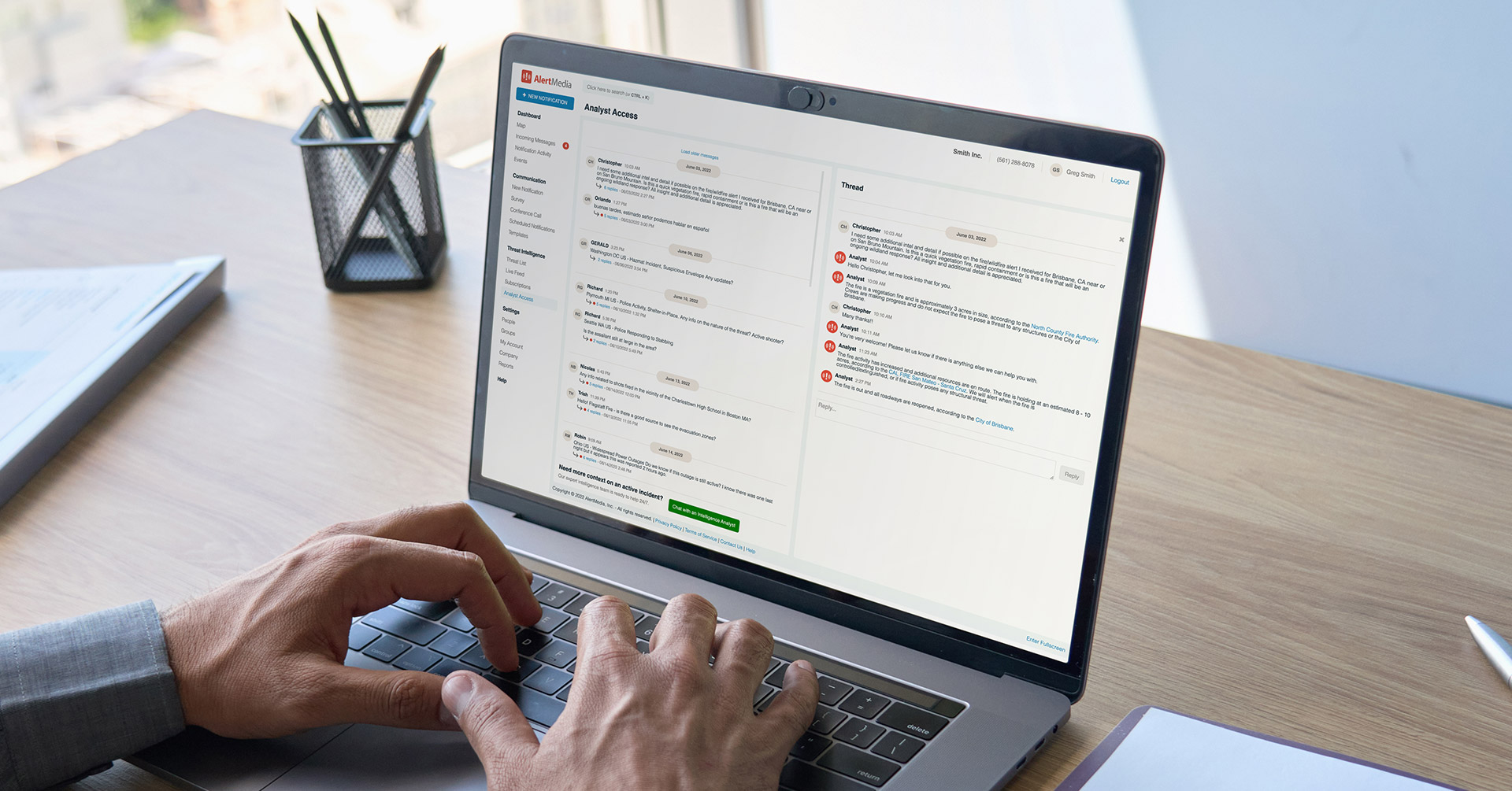
The Modern GSOC: Security in an Evolving Landscape
Coordinating disaster response is hard enough even when things go right. To tackle diverse security threats at scale, you need a robust security operations center suited to your global organization.

When a hurricane is headed straight down your path, security and safety operations can get complex quickly—especially when you’ve got people and sites all over the region. Thales Group, a multinational corporation with 50+ locations in North America, learned this first-hand.
Their emergency communication platform failed during a severe East Coast storm. As a result, they couldn’t get messages to the right people or confirm whether employees were safe when it counted most.
Coordinating disaster response is hard enough even when things go right. But it’s just one facet of the threat landscape companies face. On top of that, you’ve got cybercrime, physical security needs, and random emergencies.
To tackle these varied security threats at scale, you need experts working 24/7 to collect, analyze, and act on intelligence. A global security operations center (GSOC) fills this need, serving as a command center for large companies. But what sets a GSOC apart from other security facilities, and why is it uniquely suited for large-scale security coordination?
Find out how a GSOC differs from a security operations center, why it’s essential, and how to maximize its impact and value.
The Cascade Effect: Emerging Trends in the Threat Landscape
—Grant Hayes, COO of RBO Technology
Global Security Operations Center vs. Security Operations Center
A security operations center (SOC) is critical to organizational resilience. For many small or midsize companies with one or a few locations, a SOC can meet security needs. However, for larger companies, organization-wide security requires more than a single SOC’s capabilities (and spreading the responsibility across multiple independent SOCs creates inefficiencies).
That’s where a GSOC comes in. Much like SOCs, they’re a command center for all security, but the key differentiator between them and regular SOCs is in the name: global. They also serve a few unique purposes:
- Oversee and coordinate local and regional SOCs, network operations centers (NOCs), and operational teams
- Centralize specialized functions like fraud prevention and intelligence analysis
- Liaise with law enforcement and external intelligence sources
- Audit organizational security measures for interdepartmental gaps and malicious actor
Who needs a GSOC?
According to Grant Hayes, COO of RBO Technology, only some organizations need a 24/7 GSOC, but certain businesses depend critically on them. Grant gave us some indicators that an organization may need a GSOC:
- 24/7 working hours (or close to it)
- Frequent travel requirements
- Operations in dangerous industries
- Operations in locations with frequent threats
How to formulate your security posture
GSOCs may look different depending on your security needs, but they all serve the same core purpose: protecting your people, property, and business operations from all possible security risks. Formulate your GSOC based on your company’s specific makeup of teams, sites, physical assets, threats, and available resources. For example, threats and security needs will differ significantly between an e-commerce company and a restaurant chain.
Thales Group is a great example of how a GSOC’s structure reflects operations. Their business spans several industries, from electrical system projects with large on-site labor forces to IT services. So, to protect their people, property, and clients, their GSOC is designed to:
- Continuously monitor intelligence data to assess organizational risks
- Respond to cybersecurity risks quickly and effectively
- Advise on-site SOCs on physical security controls
—Grant Hayes, COO of RBO Technology
What are virtual security operations centers?
A virtual security operations center (VSOC) is the online equivalent of a GSOC. VSOCs are frequently outsourced solutions but can also be in-house platforms. VSOC systems integrate with your company’s security systems to detect and analyze threats remotely. Your team monitors output through a web interface with real-time access to the same information as with in-house GSOC.
VSOCs are beneficial in a few scenarios:
- For remote or hybrid workforces that need a flexible, decentralized solution
- Off-the-shelf VSOC solutions can be cheaper than investing in the infrastructure and training to build a GSOC from scratch
But they also have limitations:
- Systems integrations can be challenging and prevent making changes on the fly
- Third-party systems could become unavailable in disaster situations
- Tuning a VSOC to your company’s needs takes time and resources, which you could spend on a custom solution instead
GSOC Security Challenges & Solutions
GSOCs can be essential for organizations with a global footprint. However, operating at this scale comes with some unique challenges. Here are some key challenges GSOCs face and the solutions that can help overcome them.
Key challenges:
- Global-scale threat management—Monitoring and responding to threats across different regions, often simultaneously, can be complicated. Each region may have unique risks, requiring tailored threat detection and response mechanisms. Cybersecurity, physical security, and environmental threats may vary greatly by location, making it difficult to standardize solutions across borders.
- Time zone coordination—GSOCs often operate 24/7 and must coordinate teams across multiple time zones. This dispersed focus can result in communication delays and uneven response times. With teams operating on different schedules, ensuring seamless handovers between shifts and maintaining situational awareness can be difficult.
- Compliance with international security regulations—Security operations must adhere to local, national, and international regulations, which can vary significantly. For instance, privacy laws like the GDPR in Europe impose strict controls on data handling, while other regions may have more relaxed rules. Organizations must ensure compliance with these diverse regulations while maintaining operational efficiency.
- Data overload and incident prioritization—GSOCs often sift through overwhelming amounts of data from various sources, searching for relevant threats. This can make it difficult to prioritize real threats among routine alerts. It can also lead to response fatigue and missed critical incidents.
Solutions:
- Unified security platforms—A comprehensive and unified security platform allows GSOCs to centralize monitoring of physical, digital, and operational risks across all locations. By integrating threat data from multiple sources into a single platform, security teams can improve response times and reduce information silos. These platforms can also offer real-time insights and predictive analytics to help anticipate and mitigate threats before they escalate.
- Streamlined communication systems—To address the challenge of time zone coordination, GSOCs can implement advanced communication tools that allow real-time collaboration, regardless of location. Shared dashboards, automated reporting, and unified incident management systems ensure that teams across time zones can seamlessly share information and remain synchronized. Rotational teams and standardized handover procedures can also provide continuous coverage without gaps in response.
- Risk intelligence services & regulatory compliance tools—Adopting risk intelligence services can enhance a GSOC’s ability to manage threats globally by providing localized threat intelligence and insights. These services enable teams to stay ahead of evolving risks specific to each region. Additionally, regulatory compliance tools integrated into GSOC platforms can automate tracking and adherence to global security regulations. These tools help ensure security operations stay compliant while reducing the administrative burden on security teams.
- AI-driven analytics and automation—Leveraging AI and machine learning can help GSOCs sift through large volumes of data, automatically identifying patterns and prioritizing high-risk incidents. Automating routine tasks enables your team to focus on critical threats, saving time and resources. Using AI tools can also improve efficiency and response times.
Benefits of a GSOC
Thanks to their unique capabilities, global security operations centers help organizations achieve many of the same goals other special teams can, only faster and more effectively.
A GSOC helps your company:
- Improve threat intelligence: Threat intelligence is most valuable when fully tuned to your organization’s composition and needs. GSOC security teams have the experience and expertise to maximize usage, delivering more effective risk monitoring.
- Streamline communication: Centralizing your threat detection simplifies incident management, mainly when GSOCs can communicate with SOCs and employees via a two-way communication platform.
- Maximize resource allocation: Assigning specialized functions to your GSOC frees other teams to focus on their core strengths. Local SOCs can work on their facility’s security while the GSOC handles fraud detection and intelligence analysis.
- Prevent security gaps: A lack of clarity between physical and network security means things often slip through the cracks. A GSOC’s 360-degree view of security catches and mitigates these gaps.
- Facilitate incident response: During a large-scale emergency, security officers on the ground will have their hands full. GSOC analysts can delegate responsibilities and coordinate with law enforcement while your front-line team focuses on immediate issues.
The earlier hurricane scenario is a great example of how impactful a GSOC can be and how functions complement each other. Despite having good data on the storm, Thales group needed a better way to share actionable intelligence throughout the company. A GSOC can build a comprehensive solution to improve your company’s resilience by taking a holistic view of security and safety.
Global Security Operations Center Best Practices
GSOCs are uniquely positioned in any company’s security ecosystem, as each has specific strengths and needs. Despite those differences, here are five ways to maximize any GSOC’s impact.
Foster communication and collaboration
Most companies use GSOCs for specialized functions like identity protection, 24/7 incident response, and real-time intelligence. But its more general role as a command center—i.e., the glue holding your security ops together—is just as critical. For your GSOC to run like a well-oiled machine, operators need to master organization-wide collaboration and open communication—they have to be able to reach anyone at any time. For example:
- Interdepartmental: The GSOC’s responsibilities include everything from IT to operations to sales to HR. By sharing resources and information seamlessly, you can prevent security gaps and keep the company working toward common goals.
- Top-down: Your GSOC oversees local and regional SOCs but needs their input to perform thorough analyses. Foster open and frequent communication with SOCs, using on-the-ground reports in decision-making.
It’s easy for a GSOC to feel like the secret police, working from the shadows of a command center, but Grant Hayes stresses the importance of building a different kind of culture. Establish protocols so your workers understand the GSOC, how it relates to them, and when they can expect notifications. This transparency can generate more open communication and trust, promoting a proactive safety culture.
Grant shared a story about an oil and gas company in the South Central U.S. that faced an F4 tornado with a high risk of harm to its people and damage to its property. However, with the coordinating power of its GSOC, it was able to track the storm’s path using technology and on-the-ground reports from its employees, gathering crucial information that helped it keep everyone out of harm’s way.
Define responsibilities
As humans, we always want to avoid redundant effort. But leaving gaps because everyone “thought someone else was doing it” is even worse. To prevent both problems, your GSOC needs to define organizational responsibilities. What will your NOC handle, and what falls to the GSOC? Make a detailed list for both physical and information security management.
Let’s return to our example of a company with multiple locations on the path of an oncoming hurricane. You don’t need six different onsite SOC managers following the forecast details. It’s inefficient and could lead to conflicting decisions. Instead, the GSOC can take charge of developing actionable intelligence for company-wide use. From there, each local SOC can coordinate specific plans for its location.
Implement organizational standards
Actionable intelligence begins with accurate information. Unfortunately, inconsistent data is a common sticking point for large organizations. Departments and locations have unique terminology for facilities and equipment, usually with good reason. However, when information reaches a GSOC without the original context, inconsistencies will lead to delays and flawed decisions.
Take, for example, a server room. Your company’s locations might call it a server room, data center, IT closet, or other names. However, an IT closet could also be a storage space for spare cables, printers, and assorted parts. Now, imagine your GSOC is fielding an alarm for the IT closet at your Miami office. How critical is this alert? Is someone breaking into your data center and gaining access to sensitive equipment? Or are some power strips and a broken scanner at risk? Creating and enforcing standards avoids these issues and facilitates rapid, effective decision-making.
Global security industry regulation & compliance
Your GSOC, whether internal or external, will need to stay compliant with any relevant regulations. A complex framework of regulations and compliance standards for the entire global security industry is designed to protect data and ensure privacy.
Key regulations include the General Data Protection Regulation (GDPR) in the European Union, which sets stringent rules for data protection and privacy, and ISO 27001, an international standard for managing information security. Other regional standards, such as the California Consumer Privacy Act (CCPA) in the U.S. and China’s Cybersecurity Law, further shape compliance requirements. Ensure you follow best practices for staying compliant, including conducting regular security audits, implementing robust encryption, ensuring transparency in data handling, and maintaining up-to-date policies to reduce liability and mitigate risks.
Deploy technology
A GSOC processes mountains of information. The amount of open source intelligence alone is massive. Then, you have keycard event logs, CCTV recordings, internal communication, and other security data. Add it all up, and no human can keep up, let alone extract actionable insights.
If intelligence analysts have one claim to fame, it’s knowing how to use technology to work smarter and faster. Predictive risk monitoring is at the heart of a GSOC’s operations. But to do it successfully, you need to:
- Develop inputs such as location data, employee segmentation, and access controls
- Configure and tune alert and alarm priorities
- Implement escalation procedures to get the right sets of eyes on information in real-time
- Filter meaningless noise to prevent information fatigue
Adopt a proactive approach to security enhancements
Security professionals know that dealing with ongoing threats and incidents is a full-time job, but the key to keeping your company secure lies not in reaction but in anticipation. By preparing for potential threats, you feel prepared and not overwhelmed when a hurricane, tornado, or other crisis strikes.
With access to organization-wide data and predictive modeling tools, GSOCs can take on a variety of proactive security projects:
- Perform regular audits to test whether security policies are working as intended—for example, are keycards for old employees still active?
- Collaborate with the NOC on penetration testing, especially for emerging threats like zero-day exploits.
- Analyze organization-wide incident reports to spot hidden trends and holes in your security.
- Spearhead initiatives to keep the company compliant with security regulations.
Emerging Trends in Global Security
The global security landscape constantly evolves, whether by technological advancements or shifting workplace dynamics. Here are some key emerging trends that are shaping the industry:
Integration of artificial intelligence (AI)
AI is revolutionizing security by automating complex tasks and enhancing decision-making processes. AI-driven tools can quickly analyze vast amounts of data, recognize patterns, and identify potential security threats that might go unnoticed by human operators. From facial recognition to anomaly detection in network traffic, AI enhances physical and cybersecurity measures, providing faster and more accurate threat assessments.
Automation in threat detection
Automation is playing a critical role in streamlining threat detection and response. Automated systems can monitor networks and devices 24/7, reducing the time it takes to detect and respond to security incidents. These systems can instantly block suspicious activities, isolate compromised systems, and deploy pre-set mitigation strategies without human intervention. This automation improves the speed of response and reduces the likelihood of human error.
Predictive analysis
Predictive analysis, powered by machine learning, is becoming a cornerstone of proactive security strategies. By analyzing historical data and recognizing patterns, organizations can predict potential security threats before they occur. This forward-looking approach enables security teams to strengthen defenses, anticipate vulnerabilities, and prevent incidents rather than simply reacting. Predictive analytics also helps optimize resources and plan for future risks more effectively.
Expanding remote monitoring
As remote work models become more popular, remote monitoring technologies are gaining prominence. Advanced surveillance systems, network monitoring tools, and IoT sensors allow for overseeing facilities and digital environments from any location. Cloud-based solutions and real-time data sharing ensure that security teams can maintain visibility over operations, no matter where your people or assets are located. This trend is crucial for businesses with distributed workforces or critical infrastructure spanning multiple regions.
Continued adaptation to hybrid and remote work environments
The shift towards hybrid and remote work environments has introduced new security challenges, including securing remote networks, devices, and data access points. Companies adopt zero-trust security models, multi-factor authentication, and endpoint detection systems. Ensuring secure access to corporate resources from anywhere remains a priority, as well as providing ongoing cybersecurity training to remote employees to mitigate risks posed by phishing, malware, and other threats.
Maximizing Security Solutions in a Fast-Paced World
Every day, your company faces threats across the digital and physical realms. Your job as a security leader is to enable an effective and rapid response to nearly any risk imaginable. No one tool or solution can guarantee your success, but a GSOC is a solid foundation for a robust security posture.
Centralizing special skills and tools allows every security analyst and GSOC operator to excel at their role and collaborate on organization-wide security. With a coordinated team and thorough planning, you can meet daily, knowing you’ve built a strong security culture.