
Actionable Intelligence: Identify, Verify, and Act With Confidence
Responding to emergencies with confidence requires actionable intelligence. In this post, we’ll discuss how you can determine if the threat intelligence you’re getting is actionable and how to use it to your advantage.

No matter what threat you encounter, responding effectively requires good intel. Only clear, accurate information in context can drive confident decision-making in a crisis.
In the threat intelligence and emergency management world, we call this “actionable intelligence.” When an emergency occurs, the best intel will help you frame where, when, and how to deploy your emergency response resources. However, securing the necessary information is not always straightforward. This article offers guidelines for what makes threat intelligence actionable so you can make better decisions about intelligence sources when the stakes are high.
Download The Future of Threat Intelligence: Where AI Meets Human Insight
What Is Actionable Intelligence?

Actionable intelligence is detailed, contextualized, and strategic information about an event or situation. With actionable intelligence, you have the event data and the specific context derived from data analysis, so you can immediately move to decision-making. Many threat intelligence platforms employ expert analysts to take the raw data and make usable analysis that provides that necessary context.
For example, knowing a Category 3 hurricane is making landfall in Florida is good intel. But knowing there are 150 mph winds, widespread flooding in Miami, and a delayed evacuation from coastal cities where you have several facilities is actionable intel. You can respond specifically to the needs of your people in that area without wasting time or resources on the wrong move.
Understanding an emergency is not enough—you must act to mitigate harm.
What Makes Threat Intelligence Actionable?
While other kinds of “intelligence”—like competitive intelligence and overall business intelligence—can provide information to understand a given situation, actionable intelligence enables you to step beyond understanding and into action.
Distinguishing actionable intel from noise can be challenging. Overwhelming news feeds, raw data collection without visualization, and unverified reports can complicate the process. The expert analysis is what transforms raw data into actionable intel.
When we think about practical risk intelligence, we often consider these six components:
- Risk awareness — Recognizing the vast array of risk types
- Risk understanding — Displaying a detailed knowledge of a given threat
- Risk evaluation — Identifying the severity of a given threat
- Risk projection — Forecasting how a given threat will likely develop
- Risk assessment — Calculating the people and assets impacted by a given threat
- Risk response — Knowing how to respond to a given threat effectively
These components help evaluate the actionability of your threat intelligence. As you collect and analyze data, ask yourself questions about these aspects to enhance clarity and effectiveness.
1. Is it from an authoritative source? Actionable intelligence must come from trustworthy, authoritative sources like government agencies or established news outlets. These sources provide reliable data with accurate context, improving situational awareness.
2. Is it verified? Always verify the information before taking action to avoid disastrous consequences from bad threat intelligence. Establishing processes for internal or third-party verification ensures that you act upon substantiated claims, saving resources and preserving credibility.
3. Is it relevant? For it to be actionable, the information must apply to your situation; irrelevant details only contribute to confusion. Filtering out noise is essential to focus on the critical data you need to address an event effectively.
4. Is it timely? For intelligence to be actionable, it must be timely—received early enough to facilitate an appropriate response. Utilizing a threat monitoring system with real-time updates helps ensure that your information is current and actionable during rapidly changing emergencies.
How to Conduct a Business Impact Analysis
This video will help you facilitate an effective business impact analysis at your organization.
Other Key Components of Actionable Threat Intelligence
The questions above can help you understand if your intelligence is actionable, but there are a few other things that factor into whether or not your actionable intelligence will actually give you a leg up in your risk response and mitigation. Here are some elements you’ll want to ensure your solution or intelligence platform includes.
Raw data transformation
Raw data transformation converts unstructured data into structured formats suitable for strategic decision-making. This process involves cleaning, organizing, and analyzing data from various sources, such as social media, news media, and financial records. By applying analytical techniques, organizations can identify crucial patterns and trends that indicate potential threats, like market shifts and emerging risks, ultimately equipping them to optimize their mitigation to address these challenges proactively.
Robust verification processes
Verification processes protect organizations from threats like cyber incidents and reputational risks. Businesses must have protocols to assess claim credibility, such as cross-referencing open source intelligence data with trusted sources and using threat intelligence systems. Thorough verification of raw threat data reduces false alarms or false positives and saves resources, allowing for informed decision-making and enhanced situational awareness for your security teams.
Integration of advanced analytics
A crucial aspect of actionable intelligence is the integration of advanced analytics. Tools like machine learning and artificial intelligence enhance an organization’s capacity to swiftly and accurately analyze large data sets. These technologies help identify potential threats and opportunities teams might overlook. Advanced analytics can uncover patterns or anomalies indicating significant risks, offering a clearer view of the threat landscape. Additionally, predictive analytics allows your security teams to anticipate trends and prepare accordingly, transforming insights into strategic actions. This proactive approach ensures organizations can respond to current threats and effectively mitigate future challenges.
Pro Tip: Many threat intelligence providers rely exclusively on artificial intelligence to sort through and verify their intel. While artificial intelligence software can be beneficial when breaking down big data pools, you should look for a system that also leverages real human analysts who can independently identify and verify things AI might miss. Having trained experts is also helpful if you must follow up to get more context about a threat.
How to Apply Actionable Intelligence in Your Organization
Understanding how to apply actionable intelligence effectively is critical to maximizing its benefits across various domains, including enterprise risk management, data analytics, and more. Here are some practical applications of actionable intelligence:
Cybersecurity
Actionable intelligence isn’t just for physical threats. For cyber threat intelligence applications, organizations should continuously collect, analyze, and interpret data relating to existing and emerging threats on the dark web, such as potential malware or ransomware. Establishing processes for real-time updates on cyber threat intelligence and security postures is also crucial, as it allows teams to respond to vulnerabilities and cyberattacks proactively and deter malicious threat actors before they can exploit weaknesses.
Incident response
A structured approach to integrating actionable insights during incidents allows response teams to access pertinent information and implement timely actions. Contextual analysis is equally essential in this process. Training incident response teams to interpret tactics, techniques, and procedures (TTPs) not only empowers them to understand the nature of the incident but also improves their capacity to contain and mitigate the situation effectively.
Moreover, the value of post-incident analysis cannot be overstated. Organizations can establish a repository of lessons learned by using collected intelligence to document incidents thoroughly. This reflection phase is crucial for refining and enhancing future response strategies, ensuring that each incident contributes to a more resilient posture in the face of diverse threats. Ultimately, actionable intelligence in incident response transforms reactive measures into proactive strategies, safeguarding assets, personnel, and the overall continuity of business operations.
Vulnerability management
Organizations should implement actionable intel to support vulnerability management through continuous threat data gathering. Regularly analyzing vulnerabilities within the organization’s infrastructure based on evolving threat landscapes is essential. A risk-based prioritization approach involves classifying vulnerabilities by their exploitability and potential business impact, ensuring that limited resources focus on the most critical areas. A business impact analysis can help with this.
Proactive threat detection
Utilizing machine learning and live monitoring systems that actively interpret threat intelligence helps effectively identify anomalous behavior and other indicators of compromise. Integrating these threat intelligence feeds and threat-hunting processes with your human-vetted intelligence enhances security tools with contextual information, transforming raw data into actionable insights that refine detection algorithms. A continuous improvement approach is also crucial for effective security operations; adopting a feedback loop allows security protocols to evolve based on detected threats, minimizing potential damage before incidents escalate.
—Sara Pratley, SVP of Global Intelligence at AlertMedia
Adapting Existing Tech Infrastructures
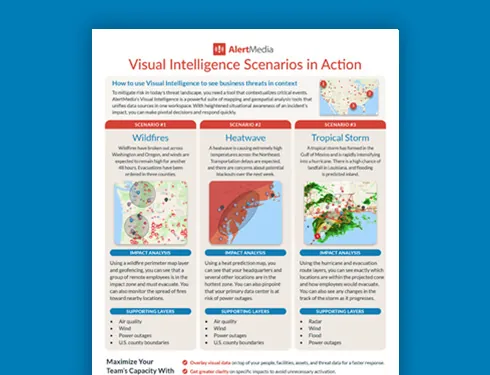
Adapting existing tech infrastructures to support actionable intelligence is crucial for organizations aiming to enhance their threat detection capabilities. This involves not only upgrading hardware and software but also ensuring interoperability among various systems and platforms. Organizations should assess their current technologies to identify gaps and opportunities for integration that can lead to improved data sharing and analysis. Cloud computing and advanced analytics tools can play a vital role in this transformation, enabling real-time data processing and collaboration across different teams.
By investing in scalable solutions that can accommodate growing volumes of threat intelligence, companies can build a resilient tech ecosystem that empowers them to respond proactively to emerging threats while maximizing their return on investment. However, no matter how advanced automated technology becomes, leading with human verification and analysis remains essential to ensure accurate threat interpretation and decision-making. As a result, organizations can maintain seamless operations, mitigate risk, and respond effectively to unforeseen challenges, thereby ensuring long-term sustainability and competitive advantage in an increasingly complex business landscape.
Challenges in implementing actionable threat intelligence
- Data overload—Organizations often find themselves inundated with vast amounts of data from multiple sources. This can lead to paralysis by analysis, where critical insights are overlooked in the sheer volume of information available, hindering effective decision-making.
- Resource allocation—Implementing actionable intelligence requires the appropriate allocation of resources, including budget, personnel, and technology. Organizations may struggle to prioritize these investments, particularly in an environment where competing initiatives demand attention.
- Skills gaps—A lack of adequately trained personnel can impede the effective use of actionable intelligence. As technology evolves, organizations may face difficulties in finding individuals with the necessary skill sets to interpret data effectively and apply insights to real-world threats.
- Integration of systems—Many organizations use disparate systems for various functions, leading to inefficiencies in data sharing and analysis. Integrating these systems to allow a seamless flow of actionable intelligence can prove to be a complex and resource-intensive endeavor.
- Cultural resistance—Organizational culture plays a vital role in implementing actionable intelligence. Employee resistance to changes, often rooted in fear of the unknown, can obstruct initiatives aimed at leveraging actionable insights for decision-making.
- Regulatory compliance—Navigating the complex landscape of data privacy and security regulations can be a significant barrier. Organizations must ensure that their methods for gathering and analyzing actionable intelligence adhere to compliance standards, which can sometimes limit their ability to respond swiftly to threats.
- Quality of data—The accuracy and reliability of the data collected are paramount for actionable intelligence. Poor-quality data can lead to erroneous conclusions and ineffective actions, making it crucial for organizations to establish stringent data verification processes.
By addressing these challenges, organizations can better position themselves to use actionable intelligence and enhance their strategic decision-making capabilities in the face of evolving threats.
Fostering Cross-Organizational Collaboration
Broad collaboration is a fundamental aspect of effectively harnessing actionable intelligence across all dimensions of business operations. Business threats often do not adhere to departmental boundaries, making it essential for diverse teams—such as IT, security, operations, human resources, and legal—to work together cohesively.
Establishing a culture of communication and shared responsibility between your security teams and other departments is vital for breaking down silos and fostering an environment of knowledge sharing. Regular joint training sessions, crisis response drills, and cross-functional meetings can enhance team cohesion and ensure that every department is well-equipped with the understanding necessary to identify and respond to various threats collaboratively.
This holistic approach fortifies the organization’s overall posture against various threats, enhances its resilience, and improves the results of your actionable threat intelligence, ensuring that operations can continue smoothly despite adversity.
—Sara Pratley, SVP of Global Intelligence at AlertMedia
Future Trends
As organizations face a complex threat landscape, several trends will influence the future of actionable intelligence. Technological advancements, especially in artificial intelligence and machine learning, will improve data processing and analysis across various domains, including health risks and supply chain issues. Globalization will drive real-time intelligence sharing across sectors for a comprehensive optimization and understanding of risks from natural disasters, geopolitical instability, and economic changes.
Organizations will increasingly adopt proactive strategies using predictive analytics to anticipate and mitigate threats. Embracing these trends is crucial for building resilient strategies and workflows to respond effectively to diverse threats in a changing global environment. By staying vigilant and adaptable, organizations can protect themselves while maintaining their bottom line and customer satisfaction during times of uncertainty.





