
Cybersecurity Awareness Month 2024—Secure Your Business and Our World
Need help upgrading your company’s cybersecurity? Here’s how you and your people can “Secure Our World” during this October’s National Cybersecurity Awareness Month.

In our hyper-connected world, cyberattacks have become a constant threat, with data breaches striking businesses across every sector. The impacts extend beyond immediate financial losses—cybersecurity incidents now threaten reputation, customer trust, and operational stability. According to IBM’s Cost of a Data Breach Report 2024, the average global cost of a data breach has risen to $4.5 million. But beyond the monetary toll, these incidents significantly undermine response time and business continuity. According to the report, it takes organizations more than 200 days on average to identify and contain a breach—leading to prolonged exposure and risk.
“We always want to be careful with what we click and what we're opening, whether it's a personal system or a corporate system.”Heather Engel Managing Partner, Strategic Cyber Partners
Particularly troubling is the impact on healthcare organizations, where breaches incur average costs of over $10 million due to the sensitivity of patient data. These breaches disrupt critical services, forcing hospitals to divert resources to recovery efforts rather than patient care. Looking beyond healthcare, the ripple effects of these breaches also hurt customer loyalty—the same report finds that nearly 40% of consumers say they stop doing business with companies that fail to protect their data.
The contemporary threat landscape is evolving rapidly, with more sophisticated ransomware, phishing, and supply chain attacks. The risks are increasing in frequency and complexity. Businesses can no longer afford to treat cybersecurity as an afterthought—during Cybersecurity Awareness Month and all year long. Investing in robust defenses and proactive incident response plans is essential to avoid the devastating costs that follow a breach. Cybersecurity needs to be integrated into your security posture.
Download Our IT & Cybersecurity Communication Templates
Why the Need for Cybersecurity Awareness Programs in 2024?
Cybersecurity is a subject that often gets derailed by popular perception and misunderstanding. Cyberattacks don’t usually look like a hacker typing away on a coding screen, trying to get into the mainframe of a website or server. Usually, it looks like an unsuspecting individual clicking a bad link from phishing attempts in email or text messages or plugging a mysterious USB drive into their computer and unknowingly downloading malicious software.
In the case of a high-profile attack on the password manager software LastPass, malicious software on an employee’s computer tracked their keystrokes and used their password to steal information.
“There are definitely organizations that are more a target of [cyber]attack: anything that has to do with money or anything that has to do with critical infrastructure. Those are always going to be under consistent and constant attack. But very often, it’s a product of opportunity,” Heather Engel, Managing Partner at Strategic Cyber Partners, told us in an episode of The Employee Safety Podcast. “Maybe it’s a hospital, maybe it’s a school, maybe it’s a government organization.”
Every company is at some level of risk for data breaches from a cyberattack. And like with LastPass, every employee is responsible for cybersecurity. That’s why the Cybersecurity and Infrastructure Security Agency (CISA) has made the theme for this year’s National Cybersecurity Awareness Month (NCSAM) “Secure Our World.” We all have an opportunity to learn from these awareness campaigns to develop good cybersecurity habits and follow the simple steps to stay safe online and protect against harmful cyberattacks. In this article, we’ve broken down a few ways you can enhance cybersecurity so your business can protect itself and our world at large.
What and When Is Cybersecurity Awareness Month?
The U.S. Government has long recognized the importance of cybersecurity. In 2001, the nonprofit National Cybersecurity Alliance (NCSA) was founded, and in 2004, the U.S. Department of Homeland Security (DHS) designated the month of October as Cybersecurity Awareness Month. Cyberattacks from Chinese government hackers were the most significant source of concern, but since then, attacks from Russian and private groups have increased dramatically.
Regardless of the cyber threat du jour, the purpose of Cybersecurity Awareness Month is to encourage a collaborative effort between the public and private sectors to increase information security by providing everyone with the tools necessary to protect their digital lives and livelihoods.
Today, Cybersecurity Awareness Month is co-stewarded by the National Cybersecurity Alliance at staysafeonline.org and CISA, a DHS agency founded in 2019 to bolster America’s ability to resist and withstand cyberattacks. The overarching theme for Cybersecurity Awareness Month 2024 is “Secure Our World,” and there are four recommended precautions that can help structure your efforts:
Strong, difficult-to-guess passwords can thwart many cyberattacks, but people often use the same password for all of their accounts. Tools like password managers can help people easily use different, strong passwords for each account.
Use tools that require individuals to sign in through a secondary device, such as a personal cell phone, to add another layer of protection to everyone’s digital activities.
More than 90% of successful hacking attempts begin with a phishing message. Train your people on how to identify and report suspicious messages.
It’s frustrating when our computers nag us to update our software when we’re in the middle of important work, but it’s also necessary. Software companies work tirelessly to ensure the safety of their users, but they can help only if you allow them to keep your software up to date.
Every year there seems to be another high-profile cyberattack that brings cybersecurity to our attention. In April 2021, there was a major ransomware attack that shut down the Colonial oil pipeline in the American Southeast. It cost the company $4.4 million in a ransom payment just to keep sensitive information from leaking to the public. Undoubtedly, more was spent or lost due to downtime and recovery costs.
In 2020, Texas-based IT software provider SolarWinds was attacked by Russian hackers who inserted malware into one of the company’s regular software updates. It was unwittingly sent out to the company’s clients, including the Department of Homeland Security, the Pentagon, the Department of Energy, the National Nuclear Security Administration, and the Department of the Treasury. Some experts estimate damages in the range of $100 billion from this single breach.
Get Prepared This October
Why focus on cybersecurity?
As we’ve seen, a dizzying array of cybercrimes is waiting to catch unaware users. And if you’re charged with ensuring an entire company’s cybersecurity, those hazards are compounded. As businesses become more reliant on an increasing number of online tools, particularly with the rise of remote work, the digital minefields laid by cybercriminals grow denser by the day. You and your organization must prioritize cyber safety in all parts of your business. It doesn’t have to be overwhelming to “Secure Our World.”
You can download the Cybersecurity Awareness Month 2024 toolkit here.
An individual’s role in cybersecurity
Attacks like these often take advantage of small gaps in security protocol. Many cyberattacks also hinge on individuals’ lack of understanding of cybersecurity and their own role in it. Some organizations focus on shoring up their technical defenses while ignoring the human component of cybersecurity. After all, you can have the most advanced IT security apparatus in the world, but if your employee uses “password123” as their login, attackers will be able to waltz right into your systems.
Know what to prepare for
As you plan to improve your cybersecurity defenses, you first need to know what to look out for. Luckily, this is an opportunity to ask for some support from the rest of your team. Gather everyone at your company who has authority or insight into the various electronic/digital critical infrastructure that your company relies on—your IT team, HR, and any software engineering managers are great starting points. This is also a great opportunity to involve physical security leaders as many cyberattacks exploit vulnerabilities in facility security. This cooperation paves the way for a converged security approach before, during, and after any potential threats surface.
With everyone’s help, perform a cybersecurity threat assessment to identify the likelihood of various risks, as well as the potential fallout of each. A threat assessment matrix can help organize and visualize this information.
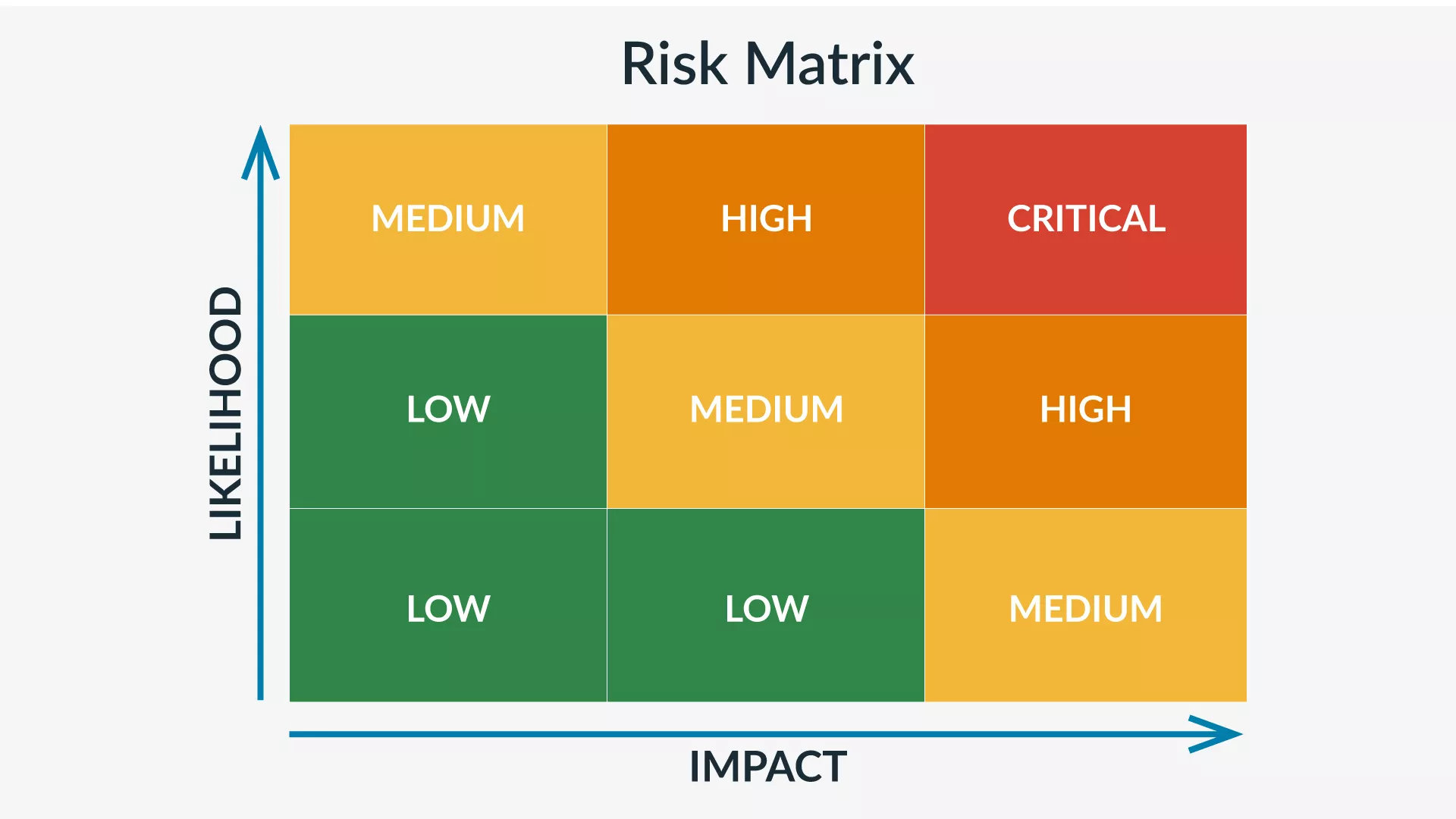
Create a cybersecurity response plan
Foreseeing potential cyber threats is a huge part of the battle. If you can anticipate the weaknesses in your systems and processes, you’re far more likely to catch any attempts to abuse those chinks in your digital armor. Staying safe means fixing those cybersecurity gaps early. Remember, the time to formulate your cyber threat response plan isn’t during a crisis but before when you have time to plan carefully and train your team.
To develop a response plan, include the same people as you did in the threat assessment step. These are your internal stakeholders who own the various digital processes that may be vulnerable to cyberattacks. Encourage them to visualize each crisis: Who should be responsible for responding to an event? How can those individuals address an active incident to mitigate harm?
Once you’re able to answer all of these questions and incorporate them into one central document, you’ll be far more prepared to resist cyber threats when and if they come knocking on your digital door. Additionally, look to outside sources to help inform your planning, such as CISA, the FCC, or even open sources of information. Document your response plan and ensure everyone has a copy of it. It’s a good idea to revisit your plans periodically to ensure they’re still up to snuff as threats and business processes evolve.
Practice makes perfect
Now that you’ve done the hard work of identifying possible cyber threats and devising responses to them, you have to make sure your plans work. Practice running drills to go over your response in a low-stakes practice environment. Go slow and allow team members to ask questions and offer suggestions. A tabletop exercise is a great way to familiarize your team with the plan, as well as to notice any potential issues that can be improved upon in the planned response. After-action reports can help you debrief and identify any gaps or areas for improvement in your plan.
Learn more about tabletop exercises
Integrating Cybersecurity Into Everyday Safety Culture
Cyber threats are often hard to notice, but they can be found anywhere. Whether you’re opening an email or logging into a service, there lurks an ever-present risk that you’re being tricked into giving up your valuable information to bad actors. As exhausting as it might sound, you and your people have to be constantly vigilant for the subtle signs that indicate someone may be trying to compromise your online safety.
A big part of cybersecurity is training your people to identify and be wary of suspicious signs and to maintain smart passwords. By providing your employees with guidance on how to spot phishing emails, for example, you can prevent attackers from gaining a foothold in your systems. Require everyone to use unique passwords for their logins and use two-factor authentication when possible.
It’s great that we have a dedicated month to come together and reflect on our online safety practices, but cyber threats don’t stop once November begins. Methods of attack are becoming more sophisticated all the time, and the demands of day-to-day work can make cybersecurity feel like a low priority. But by continually revisiting your plans and creating a culture of safety at your company, you’ll inoculate your business against hacks that can cause serious damage.




![How to Run a Ransomware Tabletop Exercise [+ Scenarios]](https://www.alertmedia.com/wp-content/uploads/2022/09/Blog-Ransomware-TabletopExercises.jpg)
