
Running Incident Response Tabletop Exercises to Prepare for Cyberattacks
Cyber threats are pervasive and becoming more challenging to prevent. Do you know how you’ll respond when under attack? Learn how to practice your incident response with tabletop exercises.

Cyberattacks seem like the threat-du-jour these days. No longer a niche hazard, our digitally dependent world is vulnerable to bad actors from around the globe.
And it’s not just government agencies, utility providers, and multinational corporations at risk. News stories drop daily, exposing organizations’ vulnerabilities—school systems and video game developers alike. Even leading information security providers like FireEye are not immune to hackers’ intrusions.
Plus, there’s more than money at stake. Many of these cyberattacks are part of a class known as ransomware attacks. When a company’s data is compromised, hackers often demand a ransom payment to unlock crucial data, but that’s just the beginning of a company’s problems. On an episode of The Employee Safety Podcast, Lori Price of Memorial Health System told us that a hack diminished their ability to transmit patient data securely and slowed down their entire organization—an unacceptable vulnerability for institutions where every second counts.
For most companies, large-scale hacks mean more money lost to downtime, recovery costs, and system upgrades. Recovering from a cyberattack is one of the highest priorities for any affected company.
Some of the easiest, most effective ways to keep your organization’s digital footprint safe are sensible rules and procedures, like password requirements and anti-phishing awareness, to avoid vulnerabilities for criminals to exploit. However, a company must also be ready to respond to a successful hack quickly and confidently. You need a strong cybersecurity incident response strategy backed by a comprehensive tabletop exercise program.
Download Our Cybersecurity Tabletop Exercise Template
What Is Incident Response?
Incident response is a company’s set of activities to respond to a data breach, locking out bad actors, recovering data, and restoring system functionality. The goal of incident response is to maintain business continuity by acting quickly and minimizing the impact of a hack.
Incident response—sometimes known as incident management or abbreviated as IR (as in IR plan)—is usually the responsibility of the IT department, but it is a team effort overall. While IT team members lead the charge, everyone else in the organization must become a stakeholder to reach common goals. After all, it takes only one person with a weak password to open the door for another attack.
What is an incident response tabletop exercise?
A tabletop exercise (TTX) challenges participants to respond to a potential incident mentally and verbally, unlike a drill that simulates the incident and challenges participants to respond in a physical capacity as well. A tabletop exercise is discussion-based and can take place in a conference room or other non-threatening environment. An incident response tabletop exercise focuses on digital security, such as a breach of sensitive company data. During this type of exercise, a facilitator will invite participants to do a mental walk-through of a cyberattack. The facilitator will present the scenario and then ask the participants what they would do in response.
The purpose of these exercises is to gauge employees’ preparedness for various safety and security threats and practice emergency response plans in a low-stress, low-cost, safe environment.
Best of all, tabletop exercises are endlessly adaptable; you can use this framework to prepare for and practice responses to all kinds of emergencies, not just the ones with “cyber-” in their names.
How to Prepare for an Incident Response TTX
Tabletop exercises are preliminary tests of security programs to help evaluate and adapt those programs for future incidents. Therefore, they’re not all that useful unless you have a plan that you’re willing to test. That means developing an incident response plan you can use in your tabletop sessions.
Four parts of an incident response plan
1. Assessment
Just as you’d look both ways before crossing the street, effective security starts with identifying risks before they become crises. A business threat assessment helps you systematically evaluate vulnerabilities, including how a data breach could disrupt operations, finances, or customer trust. By pinpointing weak spots like those below, you can prioritize safeguards before an attack occurs:
- Password phishing attempts
- Outdated or nonexistent firewall
- Cloud software provider outage/failure
After compiling this list, determine how likely each disruption is and how severe its effects would be. This process will help direct the rest of your incident response efforts.
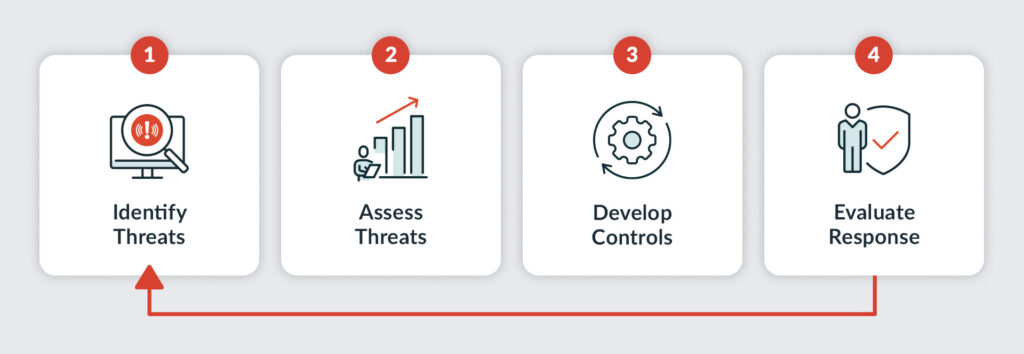
2. Identification and activation
Following the assessment step, you will identify and analyze the threats you listed to determine their early warning signs. How will you know when someone from a foreign country accesses your records? How about when one of your critical software providers, such as your CRM or HRIS vendor, goes down for hours, days, or weeks?
Incident response plans should include clear instructions on how to “activate” your plans. For example, you might install a safeguard that alerts an on-shift IT manager when a foreign IP address logs in to internal systems.
3. Containment and eradication
When malware or another threat strikes, speed and containment are critical. Your incident response plan should prioritize stopping the threat from spreading to minimize damage. This means immediately alerting employees, isolating affected systems, and disconnecting compromised devices from the network.
Communicating during a cyberattack
Cyberattacks are chaotic, disorganized moments, but your people need the right information to react appropriately. When your systems are compromised, time is of the essence, and getting an alert out to your whole company, warning them of the attack, is critical to preventing further damage.
But what if the hack took out communication tools like email? You need a way to reach everyone instantly across multiple avenues of communication, which is where an emergency mass notification system comes in. A multichannel system that can send messages via SMS, voice call, email, social media, and more is the best way to communicate during a cyberattack.
4. Recovery
Finally, you need to dedicate a portion of your incident response plan to remediation. How will your company restore backups of disrupted systems? How will employees’ access be restored? How will you restore relationships and operations with vendors, clients, and regulators? Once you’ve answered questions like these, you should compile the information from all steps in a comprehensive, centralized document.
Assessing organizational resources before the TTX
Evaluating your organization’s current capabilities and resources is critical to your preparation. This resource assessment helps ensure the exercise is grounded in reality rather than relying only on hypotheticals. It also helps identify gaps that could undermine your response to a real cyber threat.
Review your organizational resources, including people, processes, and technology. Key questions to ask include:
- Do we have the right incident response tools to detect and contain a breach?
- Are our active directory permissions aligned with least-privilege principles?
- Have we implemented multifactor authentication across all critical systems?
- Do our current policies and procedures reflect modern threat scenarios?
It’s also helpful to reference external advisories from trusted sources like CISA and use frameworks like CISA tabletop exercise packages to benchmark your preparedness. These resources can highlight best practices and emerging threat vectors.
Finally, identify and involve all relevant stakeholders, including IT, legal, HR, and executive leadership, to ensure alignment across departments. Evaluating these areas beforehand allows your tabletop exercise to reveal vulnerabilities rather than just testing assumptions.
How to Run an Incident Response Tabletop Exercise
Tabletop exercises follow a standard format that makes them easy to understand and flexible. Here’s how you would go about designing a tabletop exercise specifically oriented to incident response:
1. Design the scenario
Now’s the time for a bit of imagination. Consider the threats your incident response and cybersecurity teams have identified in your threat assessment and select the one you’d like to work on. This tabletop exercise scenario can be built around a hypothetical threat impacting your organization. Using that as a guideline, flesh out the story with some detail to make it more realistic for participants. You want this exercise to feel relatable to your employees so they can identify with it and immerse themselves in the experience.
You should start at the “identification and activation phase.” What sign alerts participants to the fact that a data breach has occurred? While planning, try to anticipate what participants might choose to do and prepare for them. You will also want to prepare injects or additional complications to add to the exercise throughout.
Potential scenarios for your incident response TTX
- Ransomware attack that encrypts core business systems and demands payment
- Phishing emails lead to compromised credentials and threaten actors’ unauthorized access to the system
- Third-party vendor breach allows attackers to infiltrate your network
- Insider threat from a disgruntled employee with lingering active directory access
- Business email compromise (BEC) results in near-execution of a fraudulent wire transfer
- Cloud misconfiguration exposes customers’ personal data to the public internet
- Distributed denial of service (DDoS) attack disrupts customer-facing applications
- Physical theft of an unencrypted company device containing sensitive data
- Exploitation of a zero-day vulnerability in widely used internal software
- Delayed breach disclosure triggers regulatory penalties and reputational damage
2. Select contributors
There are a few different ways individuals can contribute to a tabletop exercise, all of which are equally important. Those roles are:
Facilitator
The facilitator or facilitators lead the exercise. They’re tasked with presenting the scenario to participants and determining how the “world” of the scenario reacts. They shouldn’t be “presenting” as one might at a meeting. Rather, their goal is more like that of a moderator, to keep the discussion moving and to pose thought-provoking questions.
Participants
Exercise participants form the bulk of the session’s contributors. Their job is to imagine themselves in their usual roles at work when faced with a cyberattack. The facilitator encourages them to explore potential actions, ask clarifying questions, and honestly envision themselves while practicing decision-making. Remember to include members of your cybersecurity team!
Observers
As their name implies, observers do not interact directly with the participants or facilitator. Usually, just one or two people—usually key stakeholders—act as observers, passively absorbing the path of the discussion. However, depending on their expertise, the larger group might prompt them to answer questions. This person should be knowledgeable in a field such as IT, cybersecurity, law enforcement, or even digital forensics.
Evaluators
These might be the same people as the observers, or they might not, but either way, the evaluators rely on the observers’ notes. After the exercise is done, their job begins. They produce a report, much like an after-action report, that notes what went well and what you might change for next time.
3. Run the exercise
You can run the experiment once you have all the people and plans lined up. Have the facilitator present the scenario to the participants, who then act out the incident response plan. Once you run through the scenario once (which should not take longer than 30 minutes), run it again but with a changed variable, such as an important person being unavailable. A popular and effective twist is incorporating elements of converged security, i.e., on-site, real-world, physical security measures that interact with the digital world, like internet-connected cameras or digital access doors. You might also challenge participants to devise the most cost-effective solutions to a given problem.
Doing this multiple times with small changes for each run will give everyone a better idea of the many ways these situations can arise.
4. Report and improve
When the evaluators hand in their report, the cycle begins again. Ideally, the report uncovered your plan’s strengths and weaknesses, which you can use to update your incident response plan. If you commit to revisiting this incident response tabletop exercise occasionally, your plans will evolve and improve over time.
Practice Makes Protection
Every organization faces evolving threats, but proactive planning can mitigate risks. Regularly updating response plans ensures preparedness as your company grows—especially for high-impact cyber threats. Tabletop exercises bridge this gap by simulating rare but catastrophic scenarios, building muscle memory for incidents too infrequent to rely on routine training alone.

![How to Run a Ransomware Tabletop Exercise [+ Scenarios]](https://www.alertmedia.com/wp-content/uploads/2022/09/Blog-Ransomware-TabletopExercises.jpg)


