Left unchecked, small incidents can spiral into disasters. An incident management process can keep your operations running smoothly and safely.

8 Steps to Implementing an Incident Management Process

No matter how prepared you think your organization is, safety and security risks can test your plan’s limits. Ashley Guest, Head of Strategic and Operational Solutions for Trust and Security at Uber, knows this firsthand.
As Guest recounts, “One of our turning points was the explosion in Madrid in 2021. We had 30 or 40 staff members who didn’t respond to our messages. So the GSOC is doing what they should be doing: They pick up the phone, trying to engage with those staff members. One individual wasn’t directly impacted but wanted some help and support. And at the time, we didn’t have the processes in place to effectively offer that.”
From that incident, Guest knew that Uber needed to offer better on-the-ground support to employees in any location. “And I think all companies go through this learning phase,” he continues, “to understand that you don’t alleviate your duty of care by reporting that something’s gone wrong. It’s about what you do next.”
In reality, what you do next can be the difference between effectively mitigating the risk or allowing a hazard to spiral. Given the diverse threat landscape companies face, it isn’t enough to prepare plans for specific scenarios, however likely those scenarios may be. You need to be ready with an all-hazards approach and a robust incident management process.
In this article, we’ll explore how to develop an effective incident management process and review the best practices to ensure it works to keep your team secure and your business running.
Incident Response Plan Template
What Is an Incident?
An incident is any unplanned event with potential or actual consequences for your organization. It can involve cybersecurity, IT operations, physical security, heavy equipment, or any other aspect of your operations. Some common examples of incidents include:
- People gaining access to secured areas without permission
- Equipment failures causing operational disruptions
- A workplace injury requiring medical attention
- A chemical spill triggering an evacuation or hazmat response
- Heavy rain causing minor flooding near facility entrances
- An unsuccessful phishing attempt
Incident vs. accident
The terms “accident” and “incident” are often used interchangeably. But in the context of safety, security, and business continuity, the distinction is important. Both are unplanned interruptions or events, but whereas accidents always result in consequences—whether injuries, property damage, lost productivity, or other negative outcomes—incidents may or may not result in disruptive or harmful consequences. Both accidents and incidents can result in loss or damage, but incidents can also include near-misses, such as a phishing attempt that was unsuccessful at getting an employee to click on a harmful link.
The distinction matters because the term “accident” tends to focus only on events that have already caused harm, which may discourage reporting of near-misses or minor issues that could become serious if ignored. “Incident” is the preferred term in modern incident management frameworks (like OSHA, ISO 22301, or NIMS) because it encourages reporting of all types of disruptions, not just those with clear negative outcomes. This helps organizations:
- Spot patterns before harm occurs
- Improve root cause analysis
- Foster a proactive safety and security culture
Term | Harm or damage? | Impact examples | Use in incident management |
Incident | Not necessarily |
| Broad category that includes any unplanned event or disruption, whether or not harm occurred |
Accident | Yes |
| Subset of incidents that involve actual harm, damage, or loss |
Why Incident Management Matters
Incident management is what prevents an event from spiraling into a more significant emergency and risking a cascading series of consequences.
Say, for example, you’re the safety leader at a factory and your team discovers a leak in a water-coolant line. There may be no immediate risk, and dealing with the issue will involve minimal service interruptions. But if left unchecked, the leak would grow, raising the chances of the machinery overheating and breaking or causing injuries to nearby workers. Either of these situations could lead to weeks of downtime.
By addressing incidents early and diligently, you can avoid escalating risks and improve operational resilience.
What are the benefits of an effective incident management process?
- Reduces outages and lost revenue
- Leads to better service management
- Improves compliance
- Enhances employee safety
- Builds customer satisfaction and trust with vendors and stakeholders
- Reduce the likelihood of future incidents
- Helps optimize risk response strategies
Key Components of Your Incident Management System
There are three resources your organization needs to build out an incident management system.
People
Even the most sophisticated systems are useless without people actively managing them. Specifics will vary by industry and company size, but there are several core roles in an incident or emergency response team:
- Incident response leaders develop cross-functional plans, oversee major incidents from a high level, and coordinate with compliance teams to ensure regulatory obligations are met
- Security operations centers (SOCs) continuously monitor internal and external threats, assess potential impact, and deliver intelligence to inform incident prioritization and response
- Managers reinforce incident protocols within their teams, coordinate with leadership on process improvements, and ensure teams follow appropriate workflows
- IT and cybersecurity teams implement monitoring tools, manage responses to digital disruptions, and maintain secure communication and reporting systems during an incident
- Service desks and response coordinators triage incoming incident reports, escalate critical issues, and support ongoing visibility into incident status and resolution
- Frontline staff follow incident reporting protocols, provide timely situational awareness, and take prescribed actions based on the nature of the event
Tools
Incident management software helps safety teams make decisions in real-time, when it matters most. While not every incident management tool is digital or automated, online platforms will accelerate your team’s workflow:
- Incident reporting forms, whether online or on paper, allow your employees to submit the necessary information in a standardized format
- Communications platforms, including mass notification and two-way monitoring, keep information flowing quickly
- A threat intelligence platform helps your safety team understand the context in which an incident is happening
- Training videos and documentation will empower your employees to use the incident reporting system effectively
- An incident response platform can accelerate the response and manage every step of the process
Process
The next section will cover the incident management process in detail. But there are a couple key things to keep in mind:
- Like other safety and security management plans, incident response processes are living documents to continuously improve
- If your company has implemented ISO 22320, make sure your incident management plans conform to the standard
The 8-Step Incident Management Process
Here are the eight phases of the incident management lifecycle.
1. Incident identification and reporting
You can’t manage an incident if you’re not aware of it. To kick off the process, you need to understand what constitutes an incident and how to report it. There are two key aspects:
- Identification: Define what types of events your team needs to report as an incident. It’s important to collect incidents with clear consequences as well as those considered near-misses that signal potential consequences, to inform future safety plans and protocols.
- Reporting: Develop incident reporting templates to gather all of the necessary information. Along with making sure they provide thorough information, encourage employees to report incidents in a timely fashion.
2. Detection, logging, and categorization
Incidents may be reported by employees, but they’re also often identified through real-time monitoring, alert systems, or third-party intelligence feeds—especially in the case of cybersecurity, physical security, or environmental risks. Regardless of how the incident is detected, it must be logged into your incident management platform in a consistent and timely manner.
When employee reporting is appropriate, aim for an online submission system to streamline documentation. If that’s not feasible, establish a clear workflow to capture and digitize manual reports quickly and accurately.
Once the incident is logged, it must be categorized to inform how it’s escalated and managed. Categorization typically considers:
- Type: What type of event occurred? For example, data breach, workplace injury, network outage, unauthorized access, infrastructure failure, reputational threat, or natural disaster.
- Severity: How disruptive or dangerous is the event? Consider whether it’s a localized issue—such as a broken door lock—or a critical system-wide failure—such as a ransomware attack or active shooter threat.
- Impact: What are the actual or potential consequences of the incident? This could include injuries, regulatory exposure, financial loss, operational downtime, reputational damage, or a combination of these.
3. Incident prioritization and assignment
Next, your incident response team—which may include security, IT facilities, operations, or legal leaders, depending on the nature of the event—needs to prioritize the incident based on its risk profile. Use a risk matrix or decision-making framework to assess:
- Likelihood — How likely is it that the event will escalate or recur?
- Impact — What are the consequences if it does?
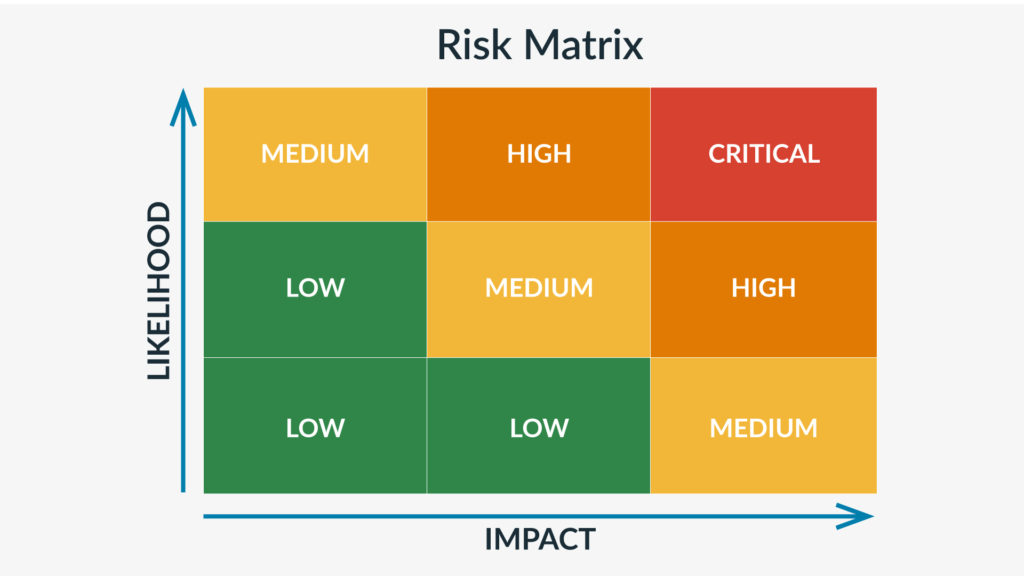
For example, a leaking drum of toxic chemicals would score high on both likelihood and impact, triggering an urgent, high-priority response. In contrast, an anomaly in a routine overnight data transfer may be low risk, requiring documentation but not immediate escalation.
After determining the urgency, your response lead will assign the incident to the appropriate point of contact. Be sure you have clearly defined roles and escalation paths for each type of incident—whether it’s a cybersecurity breach, facilities emergency, or public relations issue—and include backup contacts for urgent events.
4. Incident response
With the incident categorized and prioritized, your response team can take immediate action to contain the issue and minimize further risk. Depending on the nature of the event, this may involve:
- Isolating hazardous areas or shutting down affected systems
- Communicating impact and status updates to stakeholders
- Initiating corrective actions to begin stabilizing operations
In some cases, this response will fully resolve the problem—for example, fixing a minor coolant leak by tightening a seal. But in more complex situations, such as a system failure requiring part replacement, initial actions will serve as a temporary fix until a comprehensive solution can be implemented.
5. Investigation and analysis
Once the immediate threat has been addressed, shift focus to uncovering the root cause. This typically includes interviewing involved personnel, reviewing access logs or surveillance footage, and inspecting physical or digital systems.
For incidents involving regulatory exposure or criminal activity—such as a cyberattack or insider threat—you may need to involve internal compliance leaders or external investigators. Your goal is to determine what led to the incident and how to prevent a recurrence. Often, this step reveals opportunities to reinforce safety protocols, correct human error, or close systemic gaps.
6. Resolution and remediation
Following a thorough analysis, your team can implement long-term fixes to restore operations and mitigate future risk. For physical or operational incidents, remediation may be as simple as replacing faulty equipment or updating safety procedures.
Cybersecurity incidents or regulatory breaches typically demand more extensive actions—such as conducting full audits, notifying affected stakeholders, and updating controls across the organization. Though these efforts can be resource-intensive, they’re essential to reestablishing normal operations and trust.
7. Closure and documentation
Before declaring an incident closed, validate that all stakeholders agree the issue is fully resolved and any necessary remediation steps are complete. Only then should you move forward with documentation.
Ensure your incident record includes:
- A timeline of the event, including detection, response, and resolution
- Identified root causes and contributing factors
- Actions taken during containment and remediation
- Impacts to people, operations, systems, or assets
- Recommended updates to processes or training programs
This documentation should be accessible, standardized, and reviewed regularly to guide future responses and audits.
8. Continuous improvement
The final phase—continuous improvement—transforms your incident management process from reactive to resilient. Conduct post-incident reviews with all relevant stakeholders to evaluate performance, identify gaps, and recommend improvements.
Focus on fostering a constructive culture: use lessons learned to evolve your plans, not to assign blame. Apply insights to update training, refine response protocols, and improve system design. And importantly, share these learnings organization-wide to build operational maturity over time.
Overcoming Common Incident Management Challenges
Even with a robust incident management framework in place, organizations often encounter recurring obstacles that can undermine response effectiveness and delay recovery. These challenges typically emerge in high-stress scenarios where communication gaps, unclear roles, or inconsistent follow-through can turn minor disruptions into major setbacks. Anticipating and proactively addressing these hurdles is essential to building a truly resilient response strategy. Below are some of the most common—and preventable—challenges safety and security leaders face:
- Underreporting or delays: Sometimes, employees hesitate to speak up—whether out of fear, confusion, or just being too busy. Reinforce that reporting incidents helps everyone stay safer and smarter, not punished.
- Breakdowns in communication: In the middle of an incident, it’s easy for updates to get lost in the shuffle. Clear roles and escalation paths—practiced through regular tabletop exercises—can keep everyone aligned and informed.
- Inconsistent remediation: It might be tempting to skip a step when an incident seems small, but doing so creates gaps over time. Following through on every incident builds a stronger culture of safety and trust.
- Insufficient training: If people aren’t sure what they’re supposed to do during an incident, the entire process can stall. Keep training current, clear, and specific to each person’s role.
- Outdated response plans: As your operations grow or shift, your incident response plans should evolve too. Make reviewing and updating them a regular habit—not an afterthought.
Best Practices for Effective Incident Management
Strengthening your response capabilities isn’t a one-time initiative—it’s an ongoing process. A strong foundation will help you manage today’s risks, but staying resilient requires consistent refinement as your organization, technologies, and threat landscape evolve. Adopt these proven strategies to build and sustain a best-in-class incident management program:
- Foster a transparent culture: Make it safe and easy for employees to report what they see, share concerns, and reflect on what went wrong. Openness leads to quicker resolutions and stronger long-term performance.
- Establish clear communication protocols: Know in advance who needs to hear what—and when. A well-defined communication plan prevents confusion and keeps teams focused when it matters most.
- Leverage technology: The right tools can take a lot of the guesswork out of managing incidents. From automated alerts to centralized dashboards, technology helps you move faster and make smarter decisions.
- Invest in training: Treat incident management training as a routine—not just a once-a-year exercise. Short refreshers, integrated drills, and clear expectations go a long way in keeping people prepared.
- Track KPIs and refine continuously: Keep an eye on metrics like response time, downtime, and resolution quality. Use that data to improve—not just report on—your response capabilities.
No safety leader can foresee or prevent the threats their organization will experience. But with a robust incident management process, you can count on your team to act quickly and effectively to minimize risk and mitigate negative outcomes.
Incident Response Plan Template
More Articles You May Be Interested In
-
 Emergency ManagementInside Uber’s Incident Response Plan—Interview With an Expert
Emergency ManagementInside Uber’s Incident Response Plan—Interview With an Expert -
 Company News, Emergency ManagementIntroducing Incident Response: A Smarter Way to Manage Critical Events
Company News, Emergency ManagementIntroducing Incident Response: A Smarter Way to Manage Critical Events -
 Emergency Management, Safety and SecurityRunning Incident Response Tabletop Exercises to Prepare for Cyberattacks
Emergency Management, Safety and SecurityRunning Incident Response Tabletop Exercises to Prepare for Cyberattacks





