Threats to your business don’t stay siloed, and neither should your response strategies. Enterprise security risk management is a holistic approach to risk management.

Threats to your business don’t stay siloed, and neither should your response strategies. Enterprise security risk management is a holistic approach to risk management.

Balancing the protection of your employees, customers, assets, and data with the pursuit of business objectives is a complex challenge. In a landscape filled with external threats—from competitors to malicious actors—and internal vulnerabilities, focusing solely on defense can leave growth opportunities untapped.
How do you ensure resilience without compromising progress? Enterprise security risk management (ESRM) helps identify, assess, and reduce security risks, allowing you to manage threats efficiently while staying on track with your goals.
Enterprise security risk management (ESRM) is a holistic approach to protecting people, critical assets, and operations from all threats your organization faces. It begins with identifying threats, assessing their likelihood and impact, and implementing mitigation measures. While the process sounds simple, the scale is where the complexity lies, as businesses face millions of risks—from natural disasters and physical attacks to market fluctuations, political instability, and cyber threats. In modern security programs, these threats have grown more complex and harder to track.
ESRM emerged in the early 2000s when security experts and business leaders recognized the need for a unified approach to security as digital and physical organizational borders blurred. The term ESRM was first formally introduced in 2005 with the establishment of the Alliance for Enterprise Security Risk Management (AESRM), a joint initiative by ASIS International, ISACA, and ISSA. This risk management approach aimed to integrate physical security, cybersecurity, and business risk management into a cohesive framework.
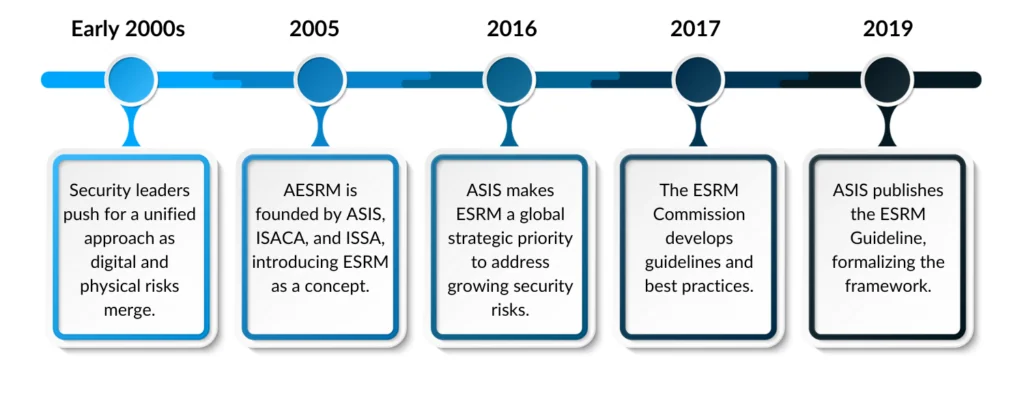
ASIS’s push to formalize ESRM in 2016 was driven by the growing complexity of security threats and the need for a more integrated, business-aligned approach. Traditional security models, which operated in silos, were proving inadequate in a world where cyber, physical, and operational risks were increasingly interconnected. With emerging threats like cyberattacks, supply chain disruptions, and insider risks, it became clear that organizations need to treat security as a strategic business function rather than a standalone concern.
In 2016, ASIS elevated the profile of ESRM by making it a key part of the organization’s global strategic plan. ASIS would go on to form the ESRM Commission, which is tasked with developing guidelines, best practices, and educational resources to help organizations implement ESRM effectively. This effort culminated in the 2019 release of the ASIS Enterprise Security Risk Management Guideline.
The ASIS Enterprise Security Risk Management Guideline is an excellent foundation for any ESRM strategy. It focuses on four key pillars for effective implementation: a risk-based approach, stakeholder engagement, continuous improvement, and data-driven decision-making.
This video will help you facilitate an effective business impact analysis at your organization.
Integrate the risk-based, data-driven, collaborative, and evolving approach ASIS advises into each stage of your enterprise risk management (ERM) framework as you…
| Step 1 — Identify risks | Step 2 — Assess and prioritize risks | Step 3 — Strategize for risk mitigation | Step 4 — Monitor and report |
It’s important to move beyond generic threats during risk identification to address the full spectrum of threats facing your organization. Exploring granular, specific details about these risks will help you develop a more effective response strategy. One proven method for comprehensively understanding threats is conducting a SWOT analysis.
A SWOT analysis is a strategic planning tool used to assess internal and external factors that impact an organization. It helps businesses identify strengths to leverage, weaknesses to address, opportunities to pursue, and threats to mitigate.
Below is an example of a SWOT analysis for a mid-sized medical supply company based in Austin, Texas.
While a SWOT analysis is useful for organizing your thoughts around known threats, it is less effective for emerging or unknown risks. This is where another pillar of ESRM excellence comes into play: data-driven decision-making.
Threat intelligence software is a powerful tool that helps organizations detect, analyze, and respond to evolving threats in real time. By leveraging data analytics, machine learning, predictive modeling, and human expert vetting, these tools provide actionable insights, allowing businesses to proactively adjust their security strategies and weigh the impact of threats.
Once you identify risks, the next step is to evaluate them based on impact and likelihood. Some risks may have a high impact but a low probability of occurring—for example, the sudden death of a CEO at a financial institution. While such an event could have severe consequences on multiple levels, the likelihood of it happening is relatively low. On the other hand, a risk with a lower impact may have a high probability of occurring frequently. However, these frequent occurrences can accumulate over time, leading to significant consequences.
A classic example of this higher-likelihood risk is phishing attacks. While a single phishing attempt may not seem like a major threat, repeated successful attacks can lead to data breaches, financial losses, and reputational damage. Over time, these relatively minor risks can compound into much larger issues for an organization.
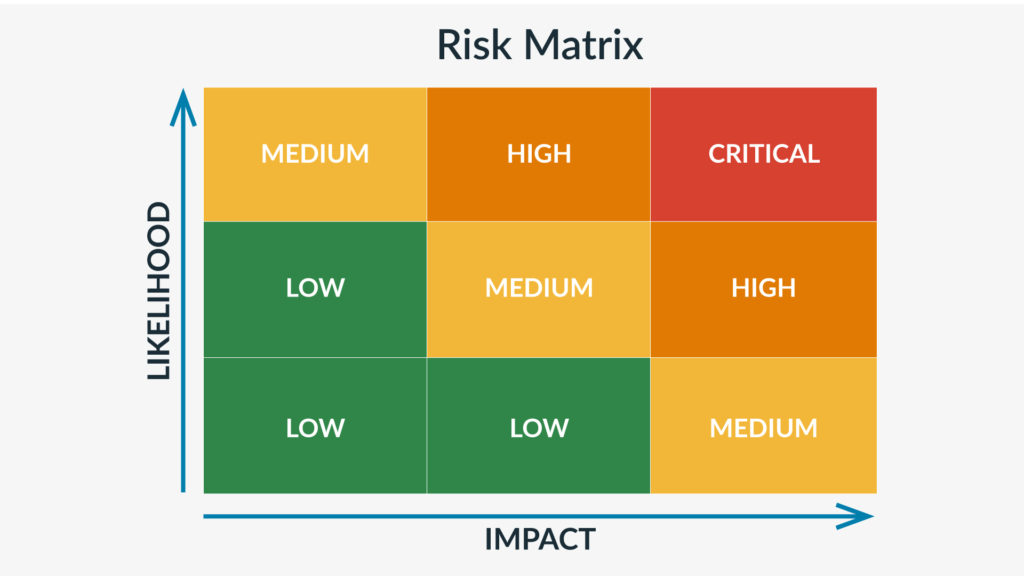
A good way to prioritize risks is to weigh them against each other with a visual aid. A risk matrix allows you to plot an organization’s risks based on their likelihood and impact. By categorizing risks into low, moderate, and high priority, a risk matrix helps decision-makers focus on the most critical threats first.

With your risks identified and assessed, it’s time to move on to the mitigation step. This is where you can return to the pillars—a risk-based approach, stakeholder engagement, continuous improvement, and data-driven decision-making—to develop incident response and business continuity plans.
Risk mitigation starts with implementing controls tailored to your risks, whether they are preventive, detective, or corrective:
Beyond technical controls, risk mitigation also requires a structured incident response and business continuity plan. Strategies like redundant infrastructure, failover systems, and resilience testing help minimize downtime and operational disruptions. Regular tabletop exercises and penetration testing refine response capabilities and improve overall security posture.
Monitoring and reporting are essential for continuously improving an ESRM framework. No security plan is perfect, and threats are constantly evolving. One of the core principles of ESRM is ensuring security strategies remain dynamic, addressing not only current risks but also those that have yet to emerge.
An intelligence-driven approach gives a clearer understanding of enterprise risk posture, allowing for better decision-making and proactive mitigation efforts. Tracking key performance indicators—such as mean time to detect (MTTD), mean time to respond (MTTR), and security control effectiveness—provides critical insight into how well a security program functions and where improvements are needed. Regular after-action reviews ensure that lessons learned from incidents or security tests translate into meaningful enhancements in resilience.
Bridget Guerrero, a security operations leader with over 30 years of experience in intelligence and corporate security, emphasizes the importance of collaboration, curiosity, and continual improvement—what she calls “The Three C’s.”
She explains how security professionals must remain adaptable and inquisitive, continuously seeking out new information and refining their response strategies. Guerrero highlights that intelligence gathering is only as effective as the context in which it is analyzed, and organizations must be diligent in verifying information before acting. Whether responding to real-time threats or assessing post-incident data, security teams must balance speed with accuracy, ensuring timely and well-informed decisions.
To learn more about how these principles can improve corporate security, listen to her full discussion on The Employee Safety Podcast, where she shares practical strategies for strengthening security operations through collaboration, curiosity, and continuous improvement.
ESRM represents a significant departure from traditional security measures, which are often siloed and managed on a department-by-department basis. As a result, successful implementation requires extensive communication and transparency across the organization. Below are some common challenges and strategies to address them.
Integrating enterprise security risk management with business continuity and resilience strengthens an organization’s ability to maintain critical operations during disruptions, whether caused by cyber threats, supply chain failures, or regulatory changes. By embedding ESRM into resilience planning, businesses can proactively address vulnerabilities, reduce response times, and improve overall risk management effectiveness.
A key enterprise risk management framework for aligning ESRM with resilience efforts is ISO 22301, the international standard for business continuity management. ISO 22301 emphasizes risk assessment, impact analysis, and structured incident response planning, making it a natural fit for ESRM-driven security strategies. For example, a company implementing ISO 22301 can integrate ESRM principles by identifying cybersecurity threats as part of business impact assessments, ensuring that data protection and system recovery strategies are incorporated into continuity plans. This alignment helps organizations maintain compliance, reduce operational disruptions, and improve their ability to respond to emerging threats.
Organizations can better anticipate threats and adapt by adopting a risk-based approach to security within the broader context of business continuity. ESRM provides the necessary structure to ensure that security measures are continuously refined, incident response is well-coordinated, and resilience planning is proactive and data-driven. In doing so, businesses can strengthen their ability to withstand crises while maintaining long-term operational stability.
Please complete the form below to receive this resource.